BlastShield™ Passive Gateway Installation on x86 hardware
Use a Passive Gateway on x86 hardwarre if you want to allow the Gateway endpoints to be able communicate freely on their local LAN whilst at the same time have secure peer-to-peer communications between themselves and other BlastShield™ nodes over the BlastShield™ network and implement micro-segmentation of access with all remote users authenticated via MFA.
Create the Gateway instance in the Orchestrator and download the bsi invitaiton file.
Download the Gateway installation package and flash it onto a USB drive.
Install the Gateway software on your x86 hardware platform.
Deploy the Gateway onto your network.
Create endpoints in the Orchestrator.
Configure an access policy and microsegmentation.
Prerequisites
Please be aware of the following requirements before you start:
You will require read / write access to your BlastShield™ Orchestrator.
Download the Gateway firmware. You can download it from here.
You will require a USB flash drive to boot your hardware from, and a monitor and keyboard to connect to your server during the installation process.
By default, the Gateway expects to receive an IP address from the network via DHCP for its public side interface. Manual assignment is also supported during the installation process.
You must have a suitable x86 hardware platform to install the Gateway software onto. Refer to the table of x86 Gateway hardware requirements for the minimum specifications.
x86 Gateway hardware requirements
Parameter | Value |
|---|---|
CPU | Minimum Intel Atom with AES-NI support or Intel Celeron with AES-NI support. Note that more powerful CPUs with AES-NI support such as Core i3 or Xeon are also supported. |
RAM | Minimum 4GB |
HDD/SSD | Minimum 8GB |
NICs | Two NICs required. Most NICs made by Intel, Broadcom and Mellanox are supported. |
The Passive Gateway may be configured with the addressing mode set to destination NAT or source+destination NAT, depending on your use case. You can choose from the options below to learn how to create the Gateway.
From the Orchestrator, select "Gateways" from the left Menu.
Select Add New Gateway from the Gateway List.
Enter a Name for the new Gateway.
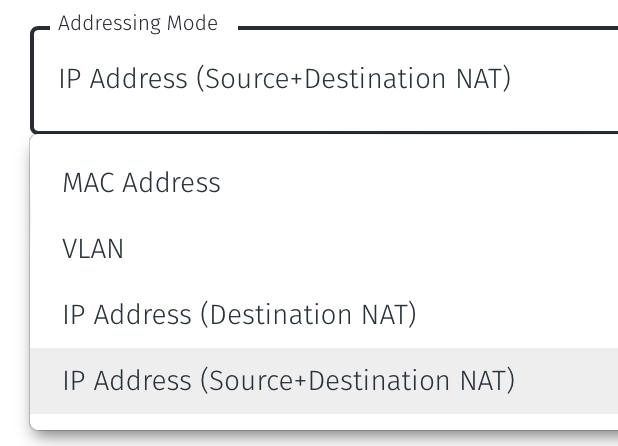
Set the Addressing Mode:
To use Source+Destination NAT addressing mode for endpoints on the Passive Gateway, chose IP Address (Destination NAT) as the Addressing Mode.
Once you have selected the addressing mode, the Gateway configuration window will update as shown below.
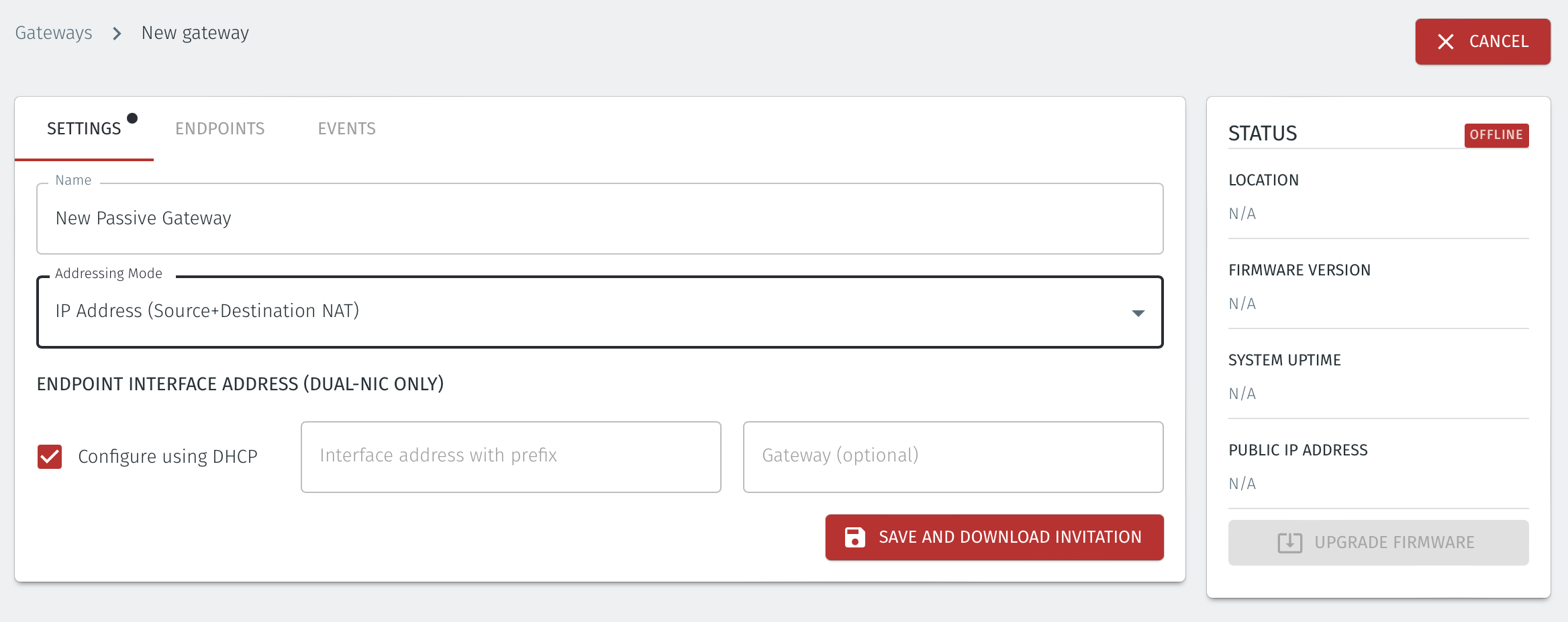
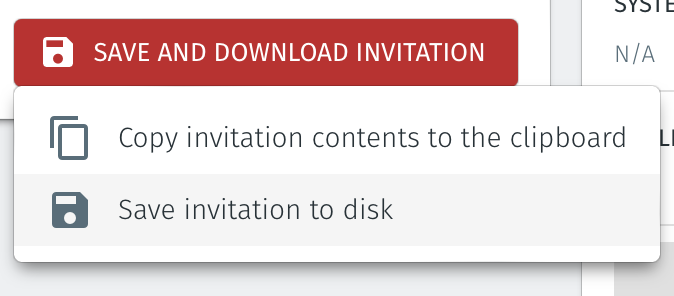
Select Save and Download Invitation.
Select the option Save Invitation to disk to download the invitation file to your local computer. You will need this file later when you flash the Gateway software to your x86 hardware.
From the Orchestrator, select "Gateways" from the left Menu.
Select Add New Gateway from the Gateway List.
Enter a Name for the new Gateway.
Set the Addressing Mode:
To use Destination NAT addressing mode for endpoints on the Passive Gateway, chose IP Address (Destination NAT) as the Addressing Mode.
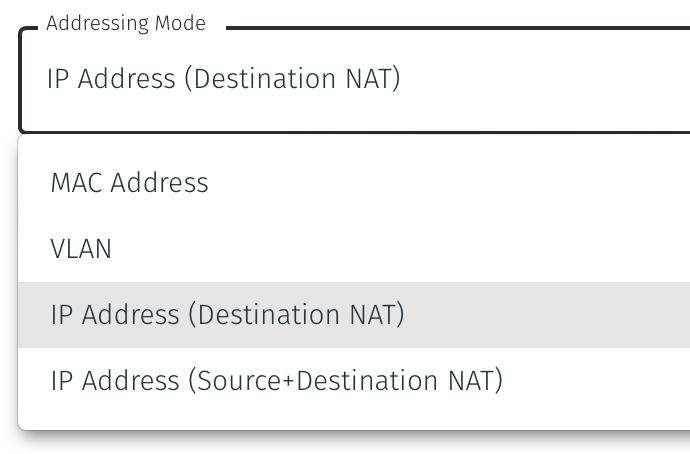
Once you have selected the addressing mode, the Gateway configuration window will update as shown below.
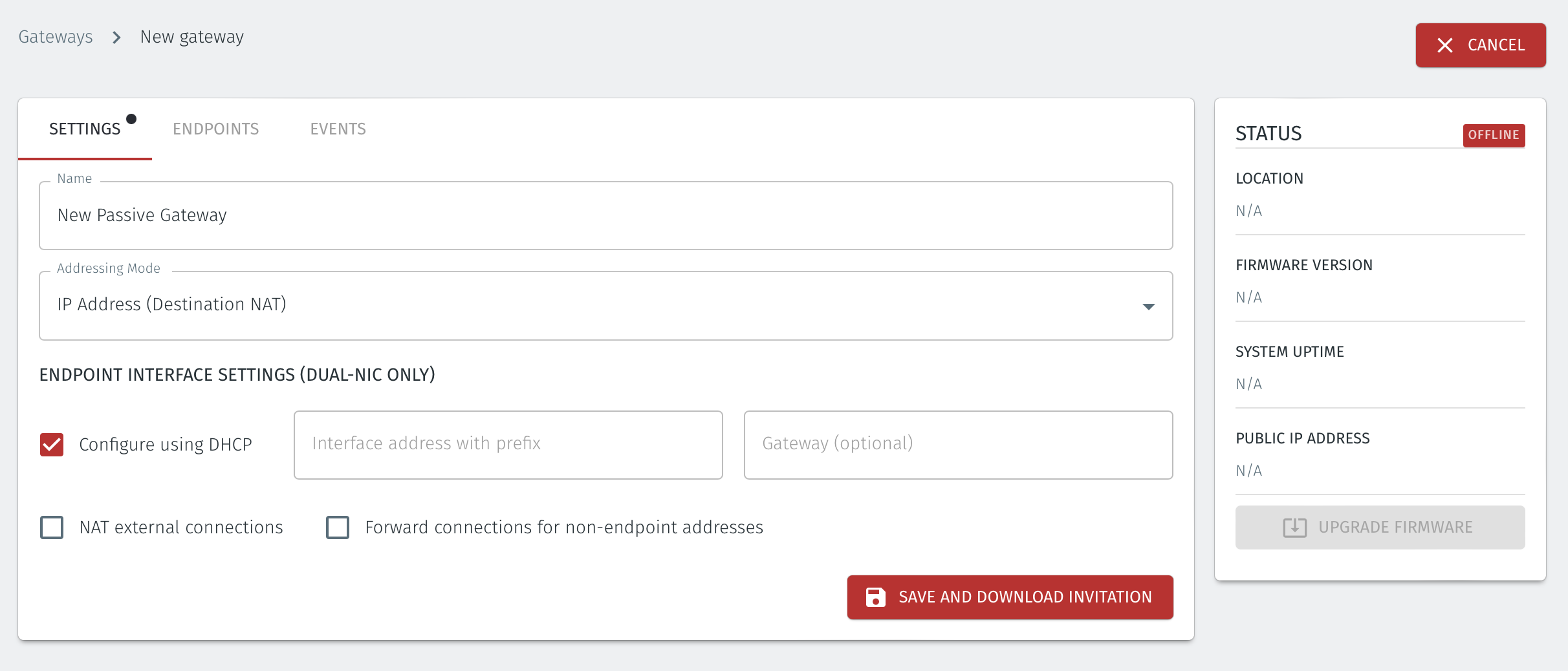
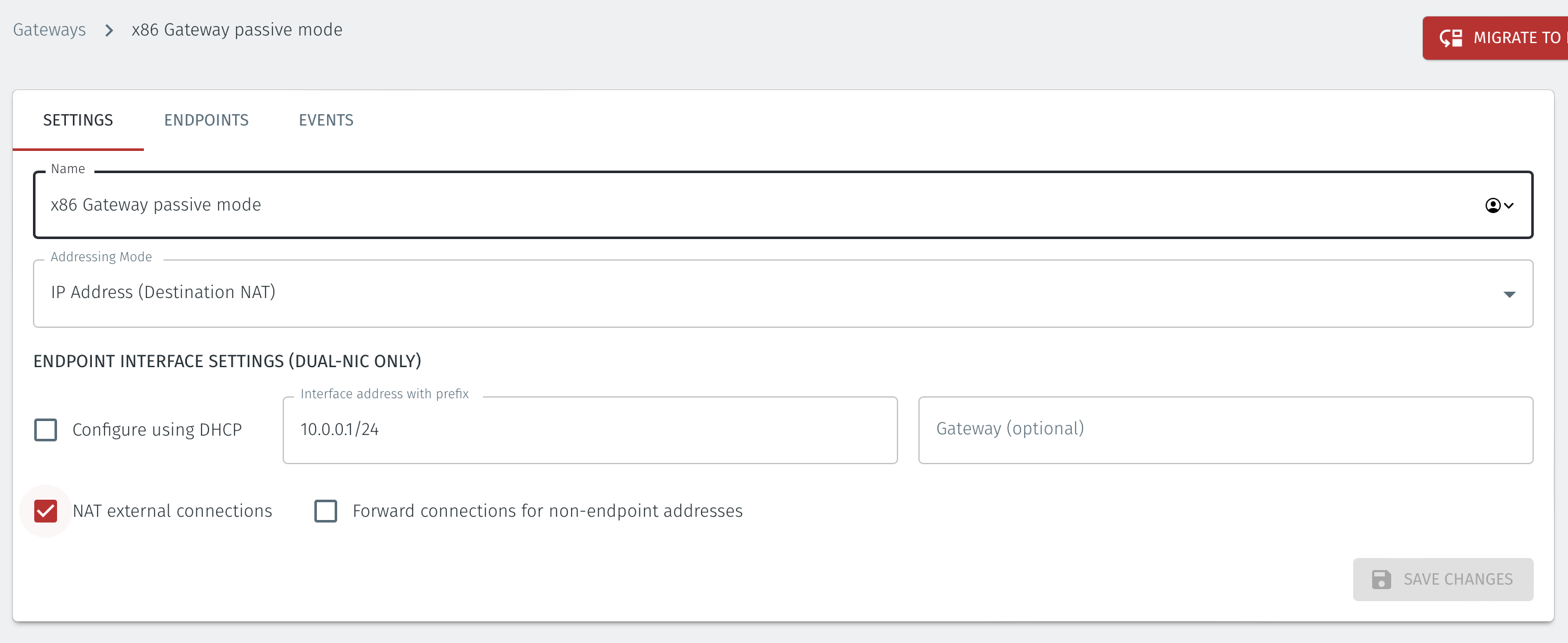
If you are using the Gateway in a single NIC configuration, leave the Endpoint Interface Settings as default.
If you are using the Gateway as a router in a dual NIC configuration, then configure the Endpoint Interface Settings:
Set the Interface address with prefix field to the same IP address as the router which the Gateway is replacing. Use CIDR format.
If you will be onboarding endpoints which are not within the subnet you specified with the interface address above, then enter the IP address of the gateway required to reach the endpoints in the Gateway (optional) field.
If you do not have a route on your internet router to the protected endpoint network, then enable NAT external connections by checking the box.
To enable the Gateway to forward non-endpoint connections from the protected network to the public side of the Gateway, check the Forward connections for non-endpoint addresses box. This will allow devices which are situated on the protected network side of the Gateway, which are not provisioned as endpoints on the Gateway, to forward traffic out.
Select Save and Download Invitation.
Select the option Save Invitation to disk to download the invitation file to your local computer. You will need this file later when you flash the Gateway software to your x86 hardware.

Download the Gateway firmware here.
Unzip the Installer Package (Do NOT run the Installer file).
Write the Installer Image to a USB drive using any available image writer
Note: there are several free utilities available for writing images to USB drives. We recommend the balenaEtcher software, but you can use any utility.
Once you have written the image to USB, copy the invitation (.bsi) file in the root folder of this image on the USB.
In this step you will be booting the x86 platform from the USB image created in the previous step.
Connect your x86 platform as shown here.
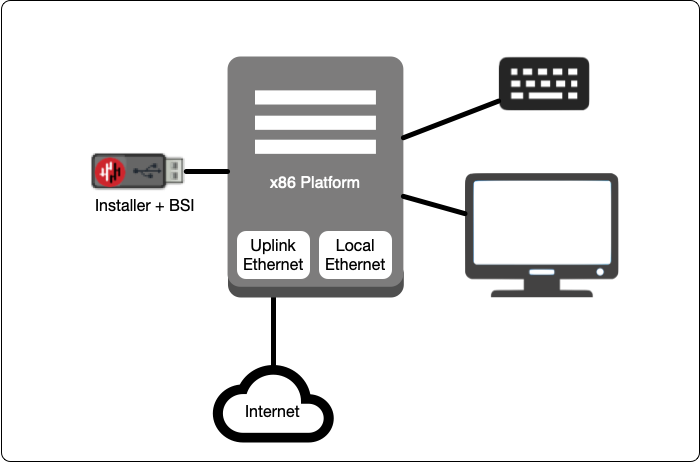
Please watch the following video or read the steps below to learn how to boot the x86 platform from the USB image.
Making sure the x86 server is connected as shown above, power it on and exit the boot sequence using the break key that applies to your hardware, then select the boot setup menu.
Re-boot your server from the USB image, once the image boots you will begin the setup process.
Select the uplink interface (to the network).
Select the downstream interface (to your endpoints).
Select the invitation (.bsi) file.
Select the target device (hard drive).
Confirm that all data will be erased and the image will be installed on the server
When the installation is complete you will be prompted to remove the USB flash drive (please remove the USB flash drive at this point), and the server will re-boot. You can disconnect the monitor and keyboard from the Gateway hardware now.
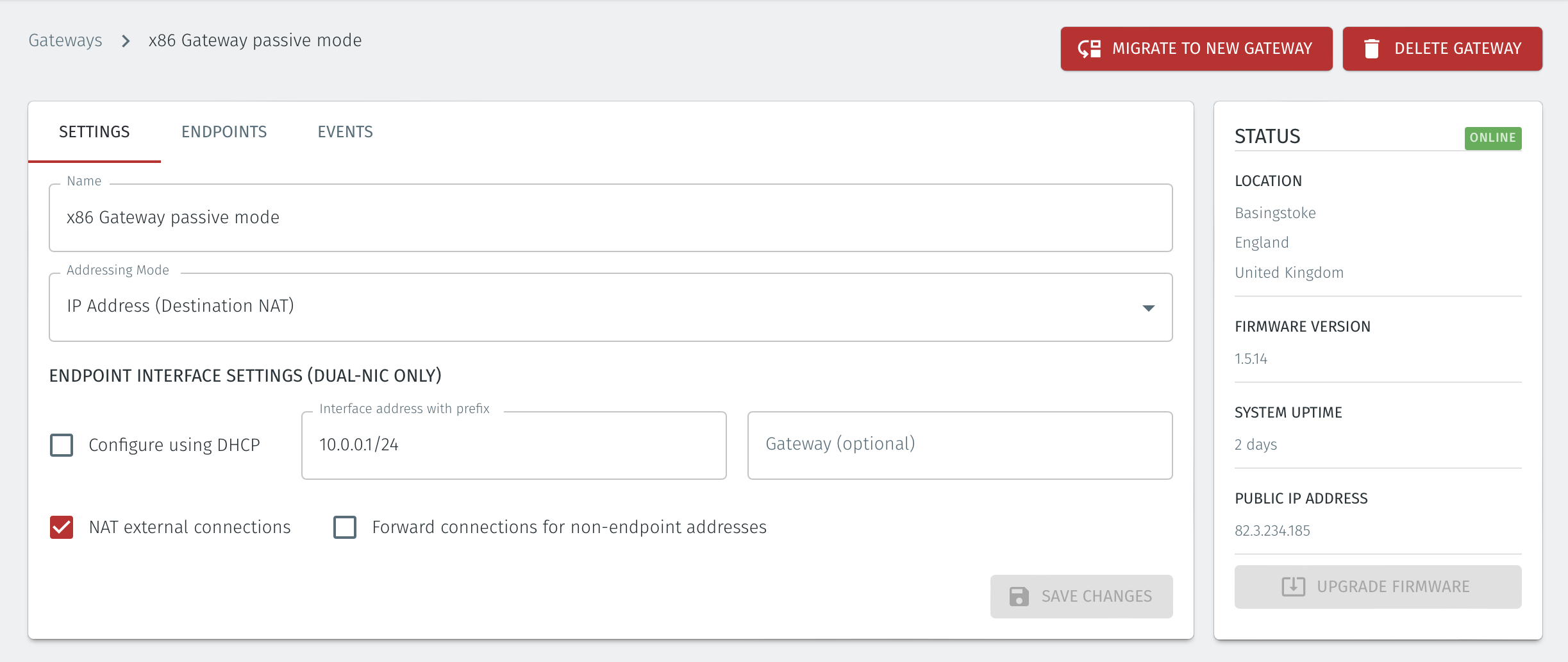
Go to your Orchestrator, and verify the Gateway status, as seen on the right hand side of the window, is now Online.
For each of the devices that you want to securely connect to the BlastShield™ Gateway, you must create a corresponding endpoint for it on the Gateway. To learn how to do this, please read the following procedure.
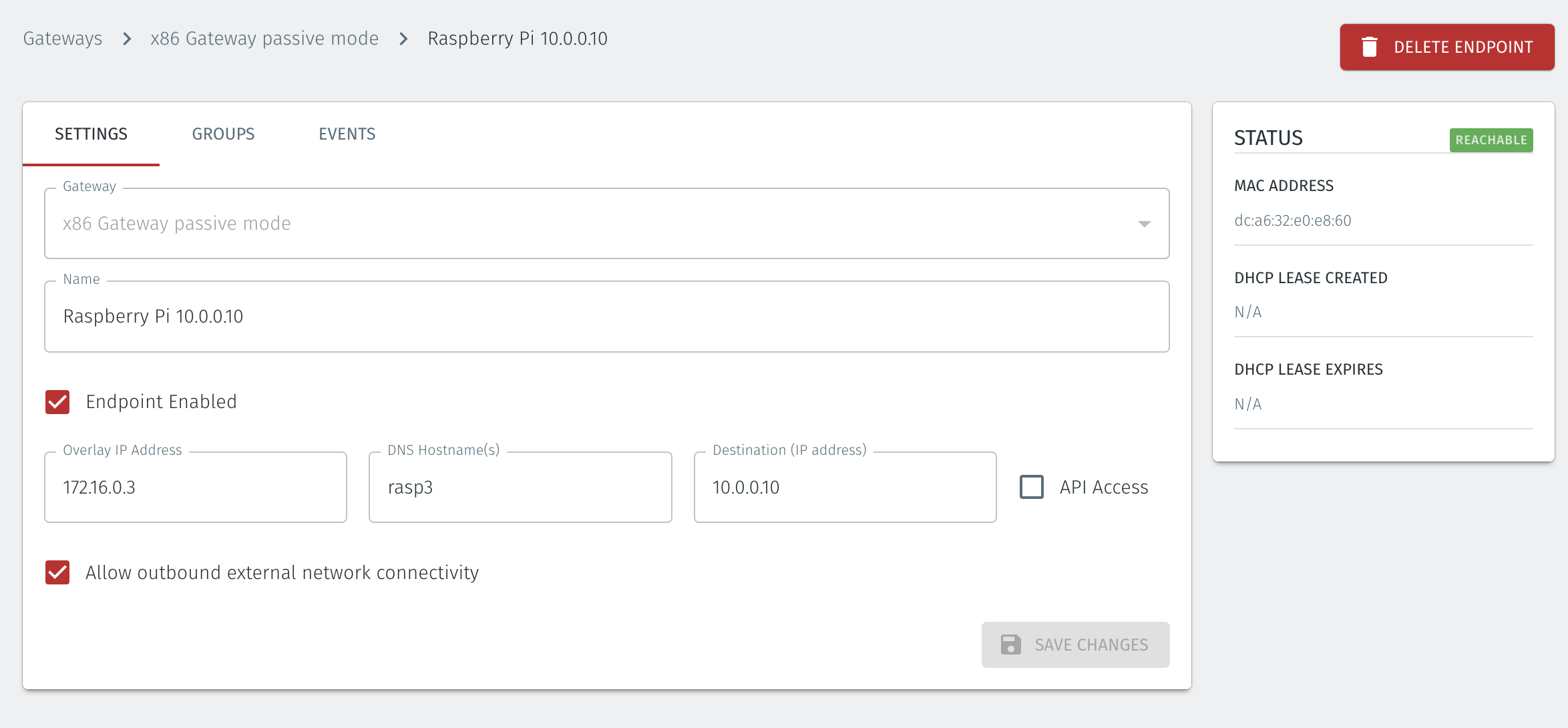
In the Orchestrator, select the Gateway which you want to add the endpoints to, and then click on the endpoints tab.
Click the 'Add New Endpoint' button and click on the 'Endpoint Enabled' button.
Enter a name for the endpoint in the Name field.
In the DNS Hostname field, enter a hostname for the BlastShield Network.
In the Destination field, enter the devices private IPv4 LAN address or hostname.
For a Gateway using Destination NAT addressing mode, If you want the endpoint to be able to communicate out through the Gateway (e.g. for transferring log files or making software updates) then check the box marked Allow outbound external network connectivity.
Click on 'Save Changes'.
The status of the endpoint will show as 'Online'.
In the Orchestrator, select the Gateway which you want to add the endpoints to, and then click on the endpoints tab.
Click the 'Add New Endpoint' button and click on the 'Endpoint Enabled' button.
Enter a name for the endpoint in the Name field.
In the DNS Hostname field, enter a hostname for the BlastShield Network.
In the Destination field, enter the devices private IPv4 LAN address or hostname.
For a Gateway using Destination NAT addressing mode, If you want the endpoint to be able to communicate out through the Gateway (e.g. for transferring log files or making software updates) then check the box marked Allow outbound external network connectivity.
Click on 'Save Changes'.
The status of the endpoint will show as 'Online'.

For endpoints on Gateways which use destination NAT addressing mode only, modify the endpoint's route table so that the endpoint may connect out over the BlastShield™ network. If you are using a Gateway which is set to Source + Destination NAT you can skip this step.
In the endpoint host, add a route to the BlastShield™ overlay network via the Gateway local LAN address.
You can verify the BlastShield™ overlay network prefix in the network settings/Overlay Subnet settings in the Orchestrator. The default overlay network prefix is 172.16.0.0/16.
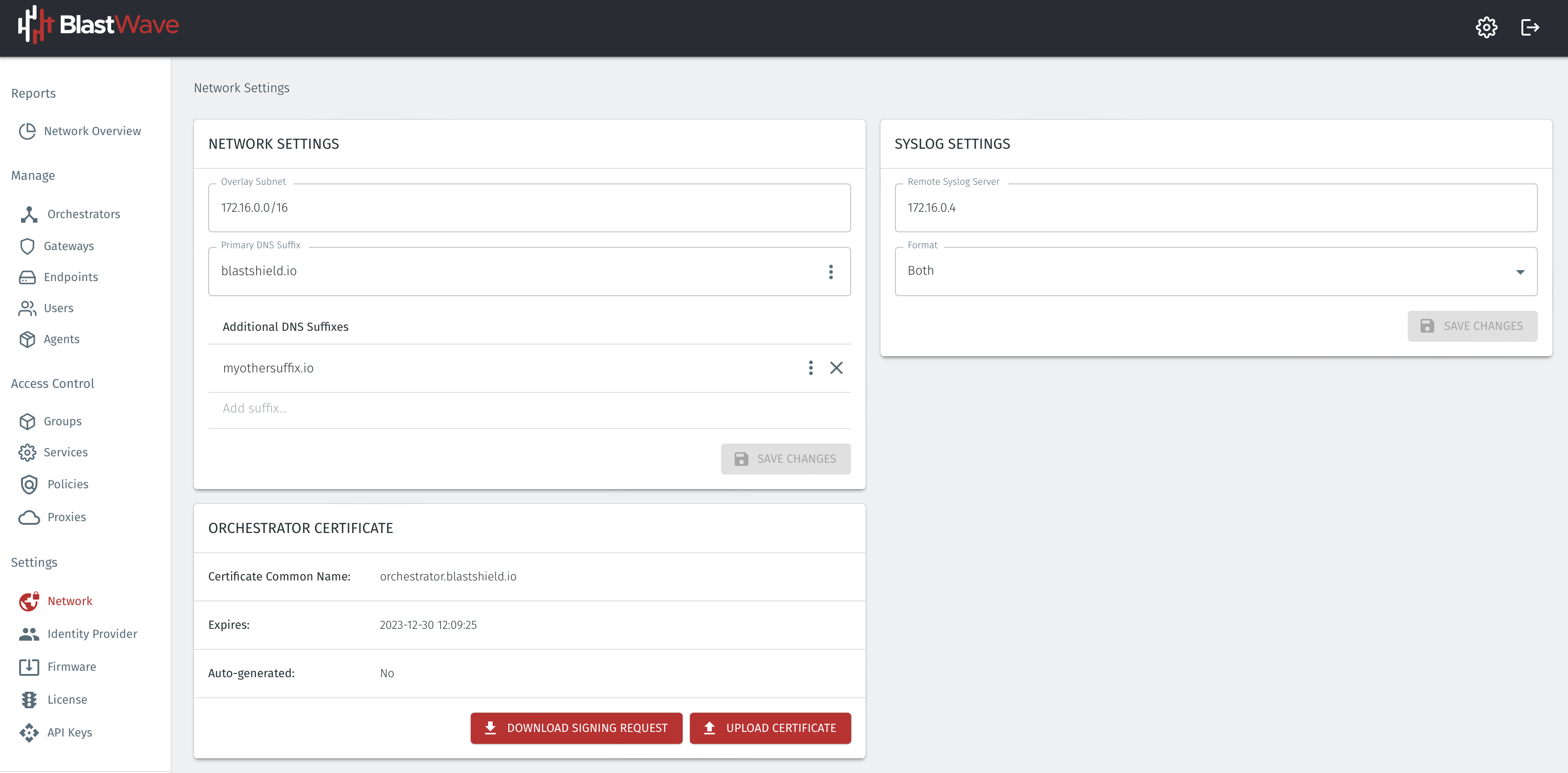
You can find the Gateway local LAN address in the Gateway settings, in the Interface address with prefix setting.
An example of the route to add in the endpoint host for this scenario would be
ip route add 172.16.0.0/16 via 10.0.0.1 [dev interface]
About Groups
Groups allow you to micro-segment users and endpoints. A group is a logical collection of endpoints and/or users that are grouped together. Groups are connected via policies, which form the foundation for BlastShield access control and segmentation management.
Any combination of endpoints and/or users can be grouped together.
There is no limit to the number of endpoints and/or users that can be in a group.
Endpoints and users can be in one or multiple groups simultaneously.
Groups are linked together via policies to provide access between endpoints.
By default, endpoints/users cannot access or have visibility to other endpoints/users unless they are granted access via a policy
About Policies
A policy defines how groups can interact. Groups are connected via policies, which form the foundation for BlastShield access control and segmentation management.
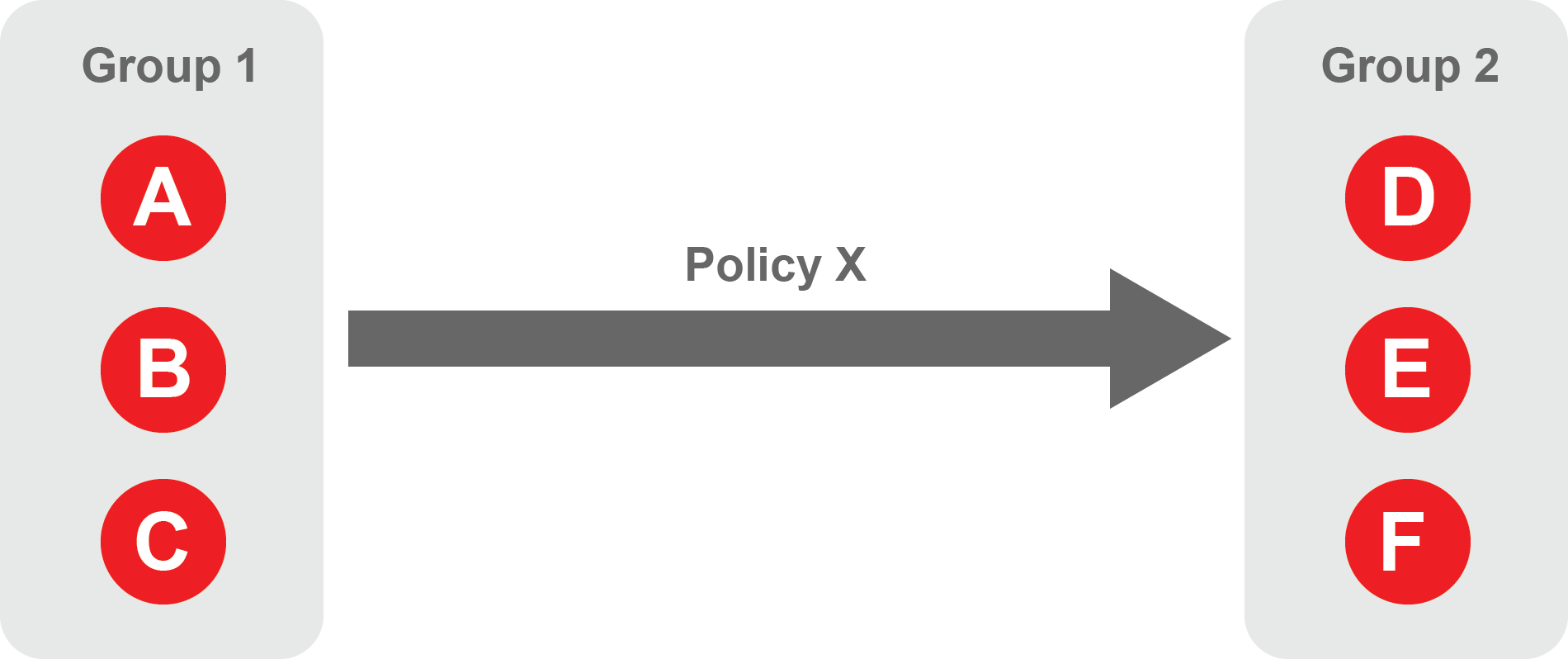
Each policy will have two sets of groups - "From" and "To".
The "From" set is one or more source groups.
The "To" set is one or more destination groups.
There is no limit to the number of groups in a given policy.
"From" Groups will have access to "To" Groups within the policy.
"To" Groups will not have access to "From" Groups within the policy.
Groups can be in one or multiple policies simultaneously.
 |
Create Groups
From the Orchestrator, select "Groups" from the left menu.
Select "Add New Group" from the Group List.
Enter a name for the new Group.
To add members to the new group, click the "Add Members" button.
If you adding users to the group then select the desired Users which you want to be associated with the Group from the "Users" box.
If you are adding Agents to the group then select the desired Agents which you want to be associated with the Group from the "Agents" box.
If you are adding Gateway Endpoints then select the desired Endpoints from the "Endpoints" box.
Alternatively, you can leave the members list empty and add/modify new members later.
Click "Add Members" to save the members.
Click "Save" to save the new group.
Repeat, if required, to ensure you have one group for your endpoints and one group for your users, which is the minimum you will need in order to define the access policy.
Please refer to the following video, which is an example of creating one group for your users and one group for Host Agents.
Create a Policy to link your Groups
Note
Users and Agents must be a member of a group for them to be used in a policy.
Select "Policies" from the left menu.
Select "Add New Policy" from the Policy List.
Enter a name for the new Policy.
Select desired "From" Groups to be associated with the new Policy.
Select desired "To" Groups to be associated with the new Policy.
Save the new Policy.
Policies are directional, so that you can control the direction in which connections may be initiated. Typically for remote access use-cases your policy would be from the "user group" to the "server group" so that users may start connections to the servers, but servers cannot start connections to users. You can create bi-directional permissions by using two policies.
The following video shows an example of creating an access Policy between a group of remote workers and a group of servers. The policy gives the remote workers authorisation to access the server group.