Using the BlastShield™ SaaS Proxy with Azure AD SSO
If you are using Azure AD as your SSO, you can use the BlastShield™ SaaS proxy to secure access into Azure AD federated M365 applications. Ensure you have already configured your SaaS Proxy as described here: The BlastShield™ SaaS Proxy Agent.
In the Azure portal, search for and select Azure Active Directory, and then go to Security > Conditional Access > Named locations.
Select Configure MFA trusted IPs.
On the Service Settings page, under Trusted IPs, choose the option for requests from a specific range of public IPs
Enter the BlastShield™ Exit Agent public IP address (you can find this in the Orchestrator, in the Status information panel of the Agent) in the format xxx.xxx.xxx.xxx/32.
Select Save.
You can configure Azure AD to skip the Microsoft MFA for users that connect via the BlastShield™ Proxy, since they will already be using BlastShield MFA for user authentication.
In the Azure portal, search for and select Azure Active Directory, and then go to User Management > MFA Settings
On the multifactor authentication service settings page, you can configure federated users to skip multi-factor authentication for the BlastShield™ Proxy Agent IP.
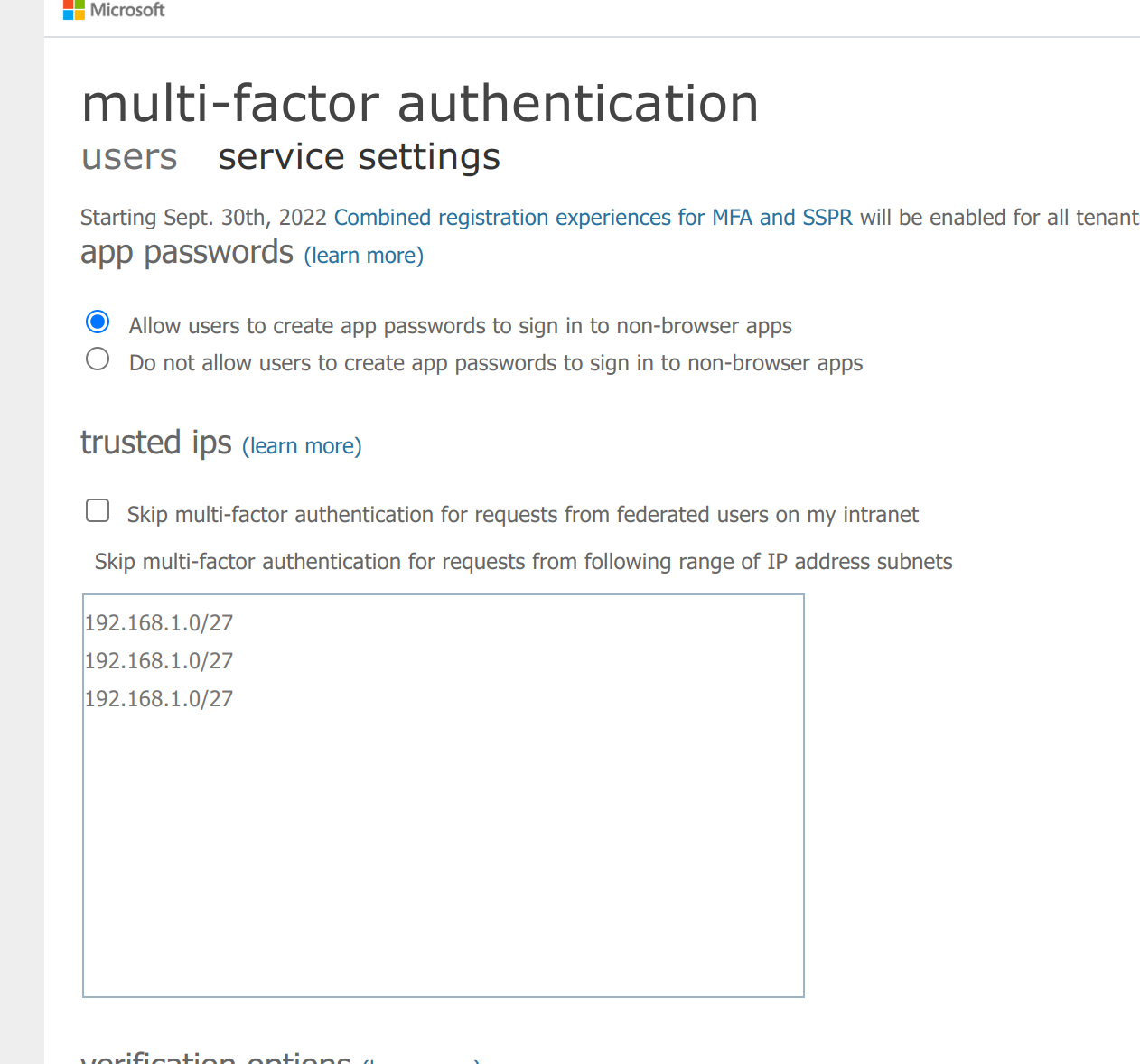
Check the checkbox marked Skip multi-factor authentication for requests from the following range of IP address subnets
Enter the BlastShield™ Exit Agent public IP address (you can find this in the Orchestrator, in the Status information panel of the Agent) in the format xxx.xxx.xxx.xxx/32.
Select Save.