Configure Azure AD as an external identity provider and use your SSO for user authentication
In this configuration, users and user groups will be provisioned by the identity provider and the user authentication will use the identity provider's SSO.
BlastShield™ is SCIM 2.0 enabled and supports integration with identity providers such as Okta, Azure AD and One Identity. SCIM support allows user accounts to be automatically created in BlastShield™ when new user accounts are assigned to the SCIM application in the IdP. User account status and their information are automatically updated in BlastShield™ based on updates in the IdP. BlastShield supports OIDC (OpenID Connect) to authenticate the SSO of the IdP for the user registration with the Orchestrator.
Your Orchestrator must have an SSO portal hostname configured for your network. Please contact support@blastwave.com to get one configured.
You must have administrative read/write access to the BlastShield™ Orchestrator and to the Azure AD configuration portal.
Outbound UDP ports to all required destinations.
If you use DNS over HTTPS, ensure it is configured in your OS and not in your browser to allow the BlastShield Client to use its associated DNS server.
Resolution of DNS requests must be supported by the network.
Ensure that the timezone is correctly set on your computer for your location and that the clock is set accurately.
Orchestrator access requires IPv6 support in the OS of the host running the desktop client, so make sure there is no Windows group policy disabling IPv6 in the registry.
Set up OpenID Authentication.
Configure the SCIM Provisioning.
Connect to BlastShield™.
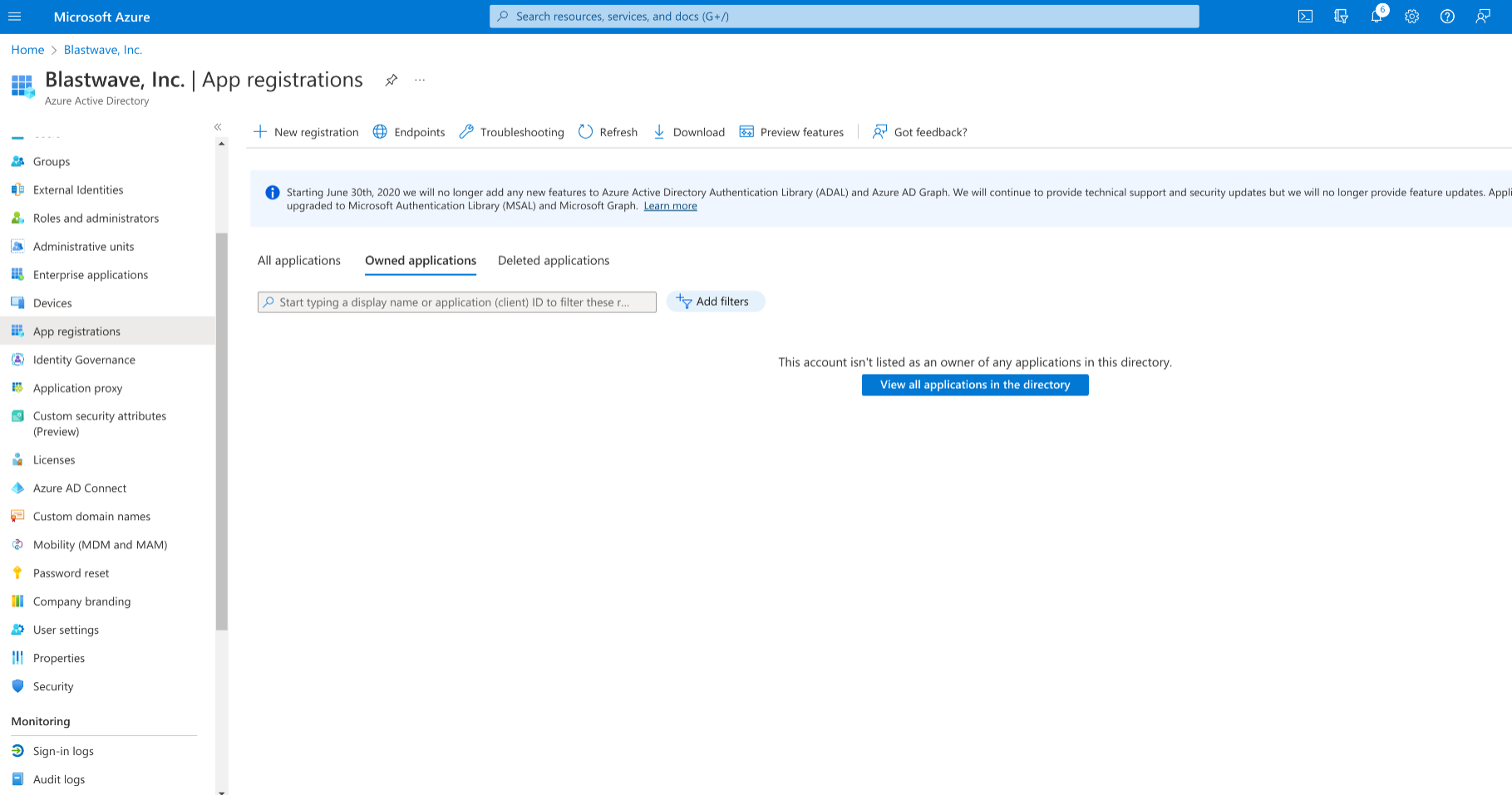
In the Azure Portal, type in “App registrations” in the top search bar and select the “App registrations” service.
Open the BlastShield™ Orchestrator in a new browser tab and from the settings menu on the left, go to the “Identity Provider” settings page.
Click on the Enable External Identity Provider checkbox.
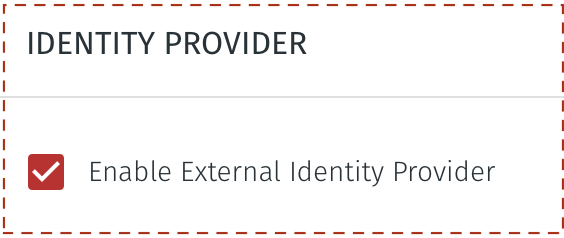
Under USER AUTHENTICATION METHOD, select the option for SSO Credentials.

Copy the Redirect URI from the OpenID section to the clipboard.
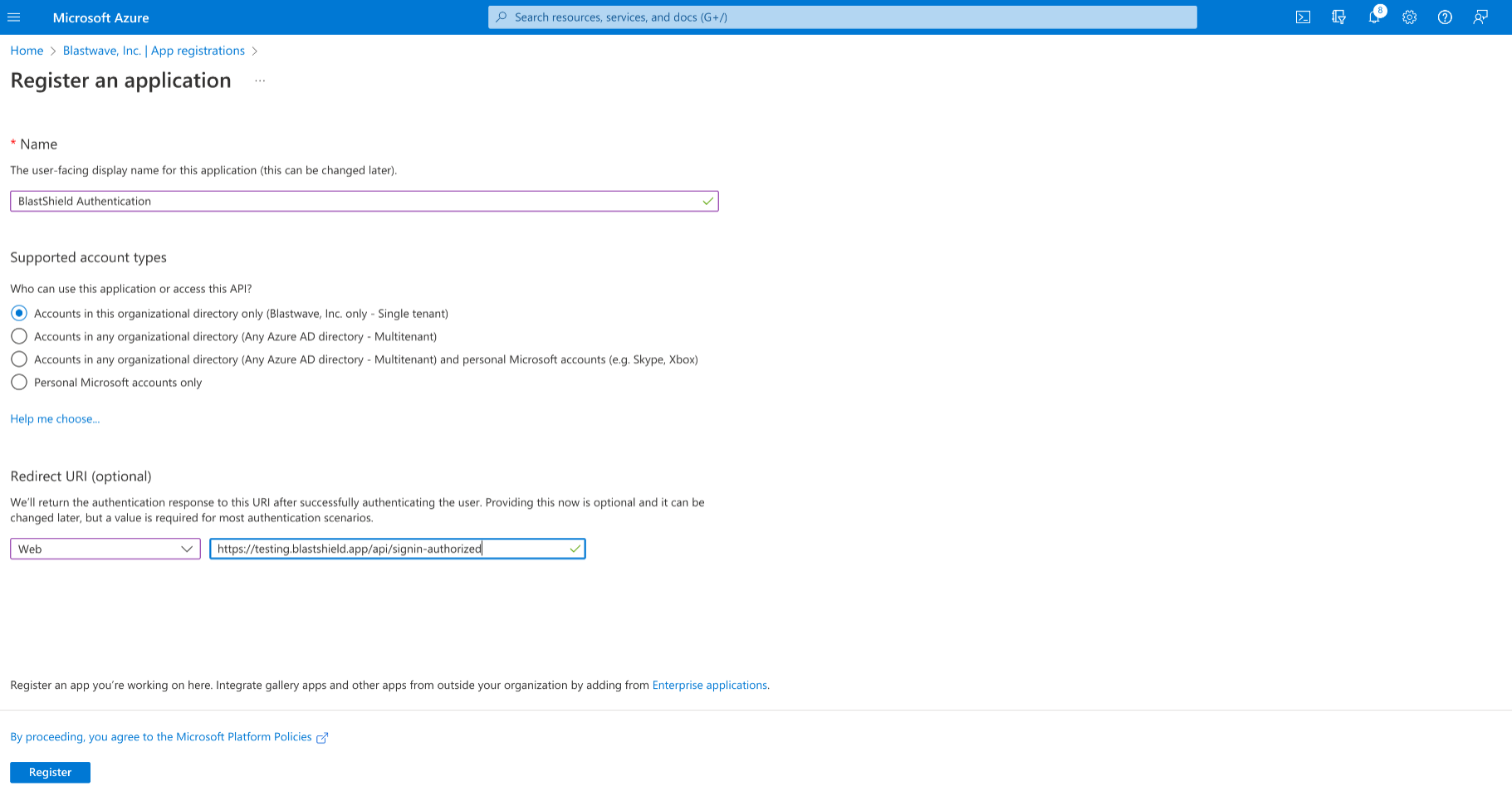
Go back to the Azure Portal tab, click on "New registration" and enter “BlastShield Authentication” as the name.
Under the Redirect URI section select “Web” from the dropdown menu and paste the redirect URI you copied from the BlastShield Orchestrator.
Click on “Endpoints” in the action bar and copy the “OpenID Connect metadata document” URL into the clipboard.
Paste the URL into the BlastShield Orchestrator as the “Domain”. Remove the extra “
https://” from the beginning of the URL and remove "/.well-known/openid-configuration" from the end.Under the “Essentials” section copy the “Application (client) ID” value and paste it into the “Client ID” field in the BlastShield Orchestrator tab.
Click the “Add a certificate or secret” link next to “Client credentials”.
Select “New client secret”, then click on Add in the newly opened right hand popup.
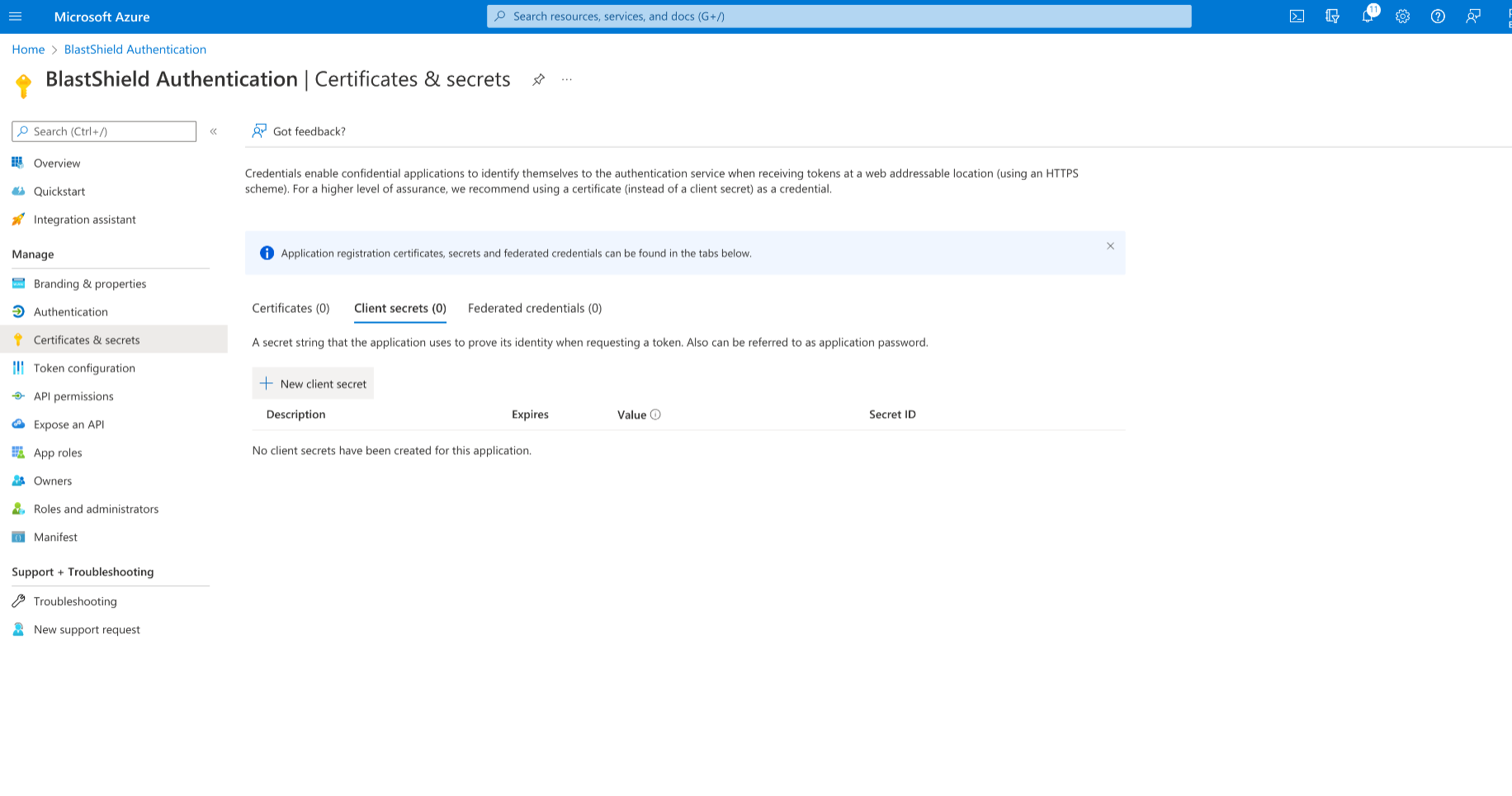
Copy the client secret value to the clipboard and paste it into the BlastShield Orchestrator as the Client Secret.
From the left-hand menu select “Expose an API”, click on “Add a scope” and enter “
api://BlastShield” as the “Application ID URI”. Select “Save and Continue”As the “Scope Name” enter “Register”.
Select “Admins and users” for “Who can consent?”.
Enter “BlastShield Authenticator Registration” for “Admin consent display name”, “Admin consent description”, “User consent display name” and “User consent description”.
Click on “Add scope”.
From the left-hand menu select “API permissions” and click on “Add a permission”. Select “My APIs” and click on “BlastShield Authentication”. Check the “Register” permissions checkbox and click on “Add permissions”.
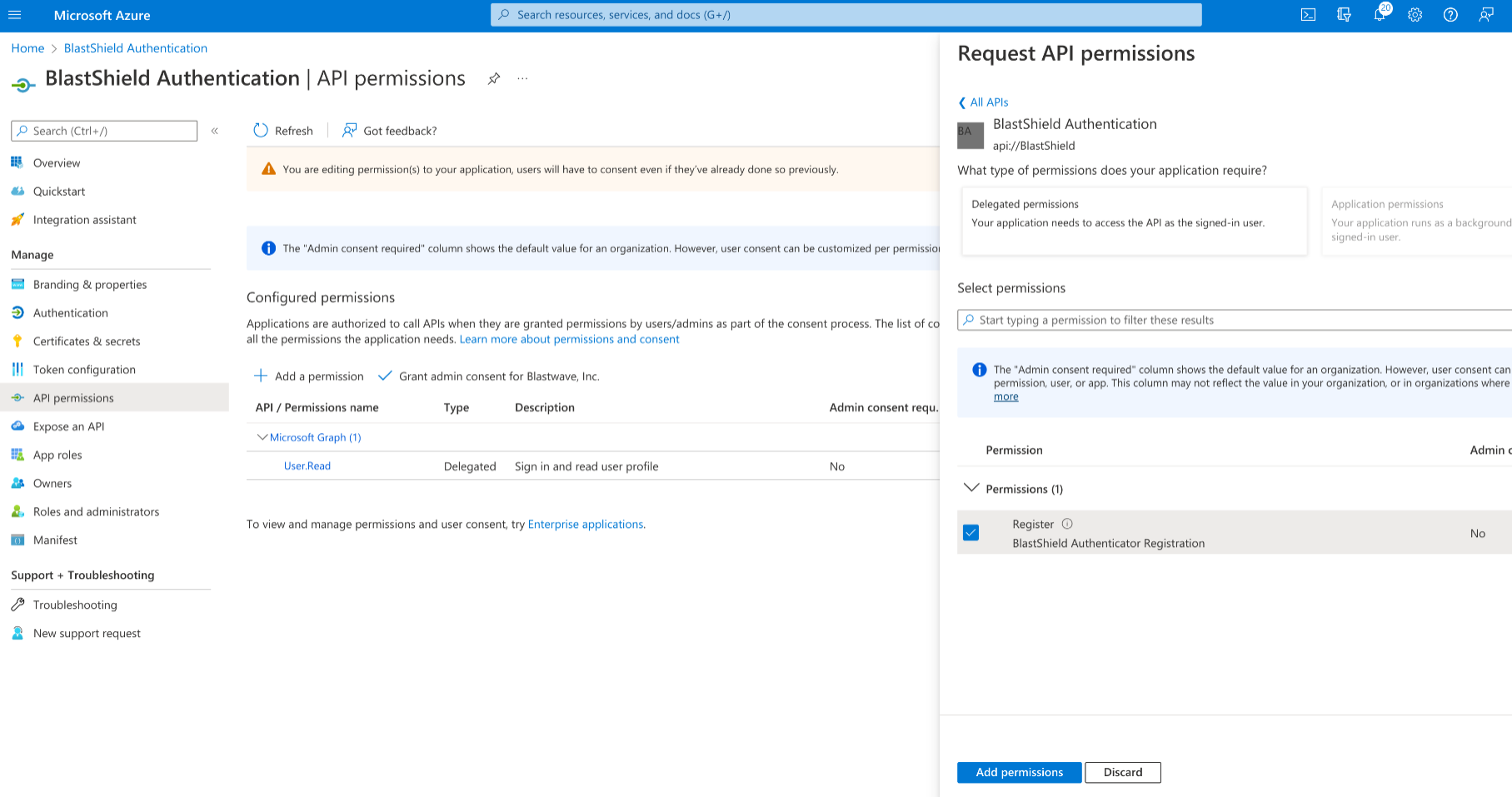
In the BlastShield Orchestrator, enter “
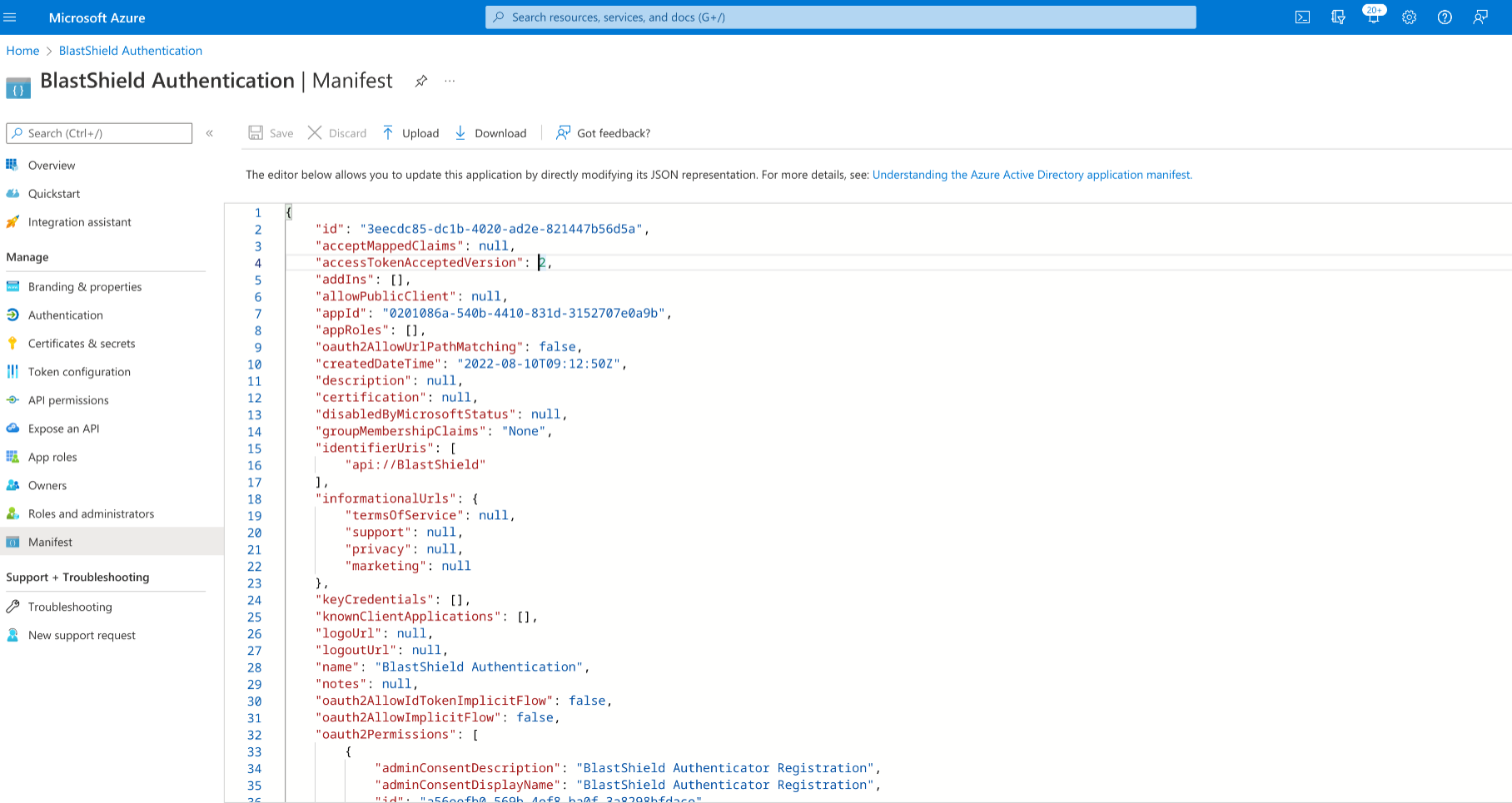
api://BlastShield/Register” as a “Custom Scope”.In the left-hand navigation select “Manifest” and in the JSON, set “accessTokenAcceptedVersion” to 2 and click on “Save”.
Type “Enterprise applications” in the top search bar and select the “Enterprise applications” service.
Select “BlastShield Authentication” and click on the “Users and groups” link in the navigation menu. Assign the application to the appropriate set of users and groups.
In the Azure Portal, type “Enterprise applications” in the top search bar and select the “Enterprise applications” service.
Click on “New application” and then select “Create your own application”.
Enter “BlastShield” as the name of your app and select “Integrate any other application you don't find in the gallery (Non-gallery)” and click “Create”.

Select “Users and groups” in the left-hand menu and assign the appropriate set of users and groups. The same set of users that was assigned to the “BlastShield Authentication” application should be used.
Select “Provisioning” in the left-hand menu and click on “Get Started”. Select “Automatic” as the “Provisioning Mode”.
From the BlastShield™ Orchestrator copy the “SCIM Endpoint” URL and paste it into the “Tenant URL” field in Azure.
In the BlastShield™ Orchestrator click on “Generate Token” next to the SCIM Endpoint URL and copy the token to the clipboard. Paste the token into the Azure “Secret Token” field.
Click “Save Changes” in the BlastShield™ Orchestrator and then on “Test Connection” in Azure to make sure the connection is working.
Select “Save”.
Click on “BlastShield|Provisioning” in the top menu and select “Start Provisioning”.
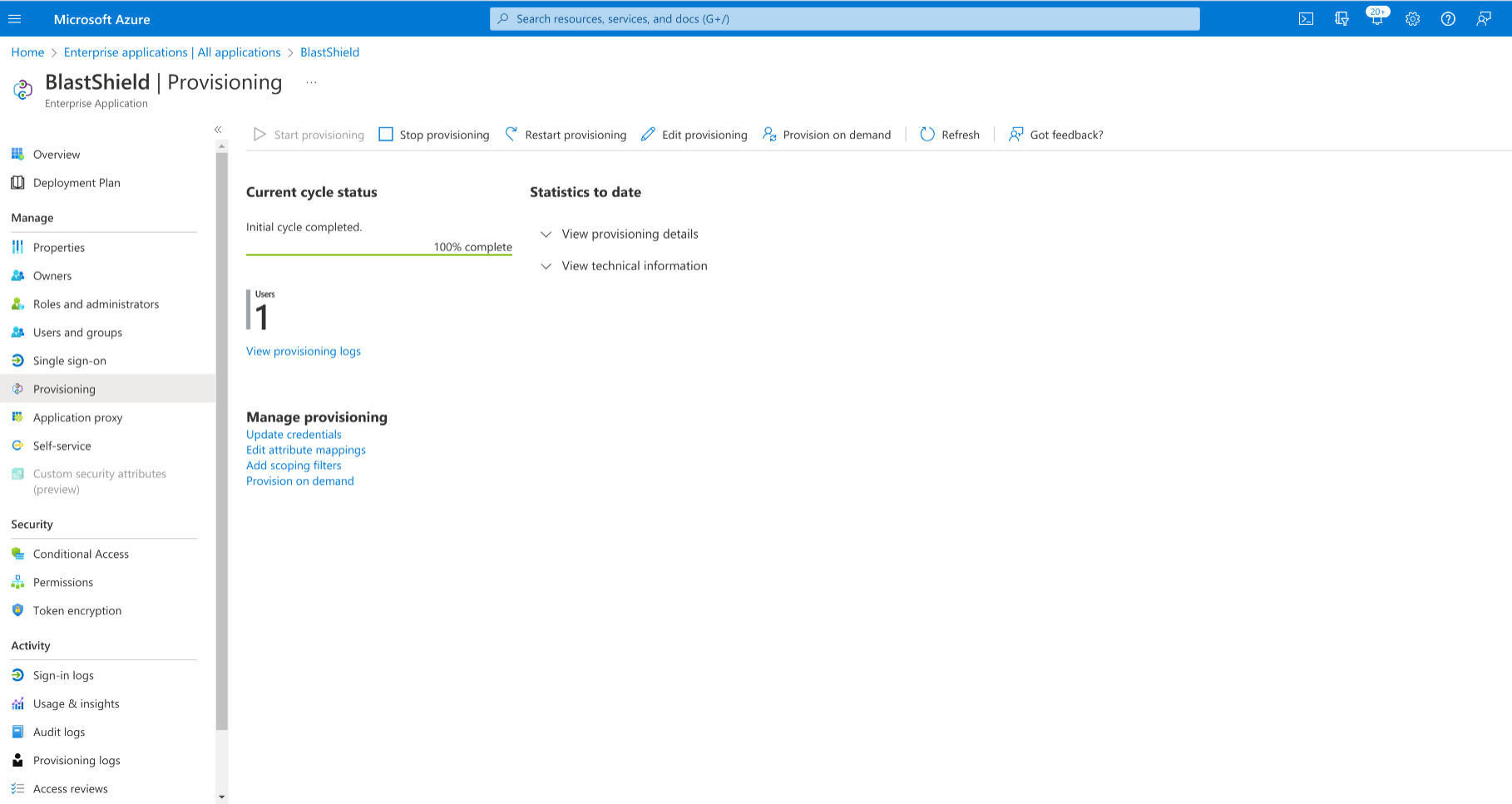
You can optionally select “Provision on demand” and select a user or group for quicker provisioning to test the setup.
Note
When this configuration is completed, users and groups which are assigned to the BlastShield™ application in Azure will be automatically provisioned into the BlastShield™ Orchestrator, and will be available to use in BlastShield™ policies. It is not possible to modify the provisioned groups from the Orchestrator, but you can add a provisioned user to Blastshield™ created groups.
Connect to BlastShield™ using the Desktop Client
To learn how to register a new user, please follow the link: Remote User Access using an SSO for user authentication