Firmware Version 1.5 Release Notes
Release Date: 22nd August 2022
Firmware release 1.5
New Features
Secure access to SaaS applications.
Extended access logging.
Support for fully air-gapped deployments.
Enhanced support for Gateway endpoint connectivity.
Added scheduled removal of user, agents and gateways.
Added support for resolving DNS records using fallback resolvers when a hostname is not assigned to a BlastShield endpoint.
It's now possible to configure a static IP address on the endpoint interface on dual-NIC NAT gateways.
Bug Fixes
Fixed a policy compilation bug when combining port-based IP protocols with generic IP protocols in a single policy (i.e TCP and ICMP).
Components to be upgraded
New firmware is available for the following applications.
BlastShield™ Orchestrator.
BlastShield™ Gateway.
BlastShield™ Agent.
BlastShield™ Desktop client.
Feature Descriptions
Secure access to SaaS applications
BlastShield™ Secure SaaS Proxy
BlastShield™ can secure access to SaaS applications such as Microsoft 365 using its zero-trust methodology combined with password-less multi-factor user authentication (MFA). Using a Proxy Agent running on a server, BlastShield™ will secure the application authentication traffic. The domains to be secured are configurable in the Orchestrator and you can proxy different sets of domains for different users. Combined with conditional access controls in the SaaS application, you can use BlastShield's zero-trust access to extend the security perimeter of your SaaS application. All user activity is monitored by BlastShield™ and may be exported to syslog for analysis.
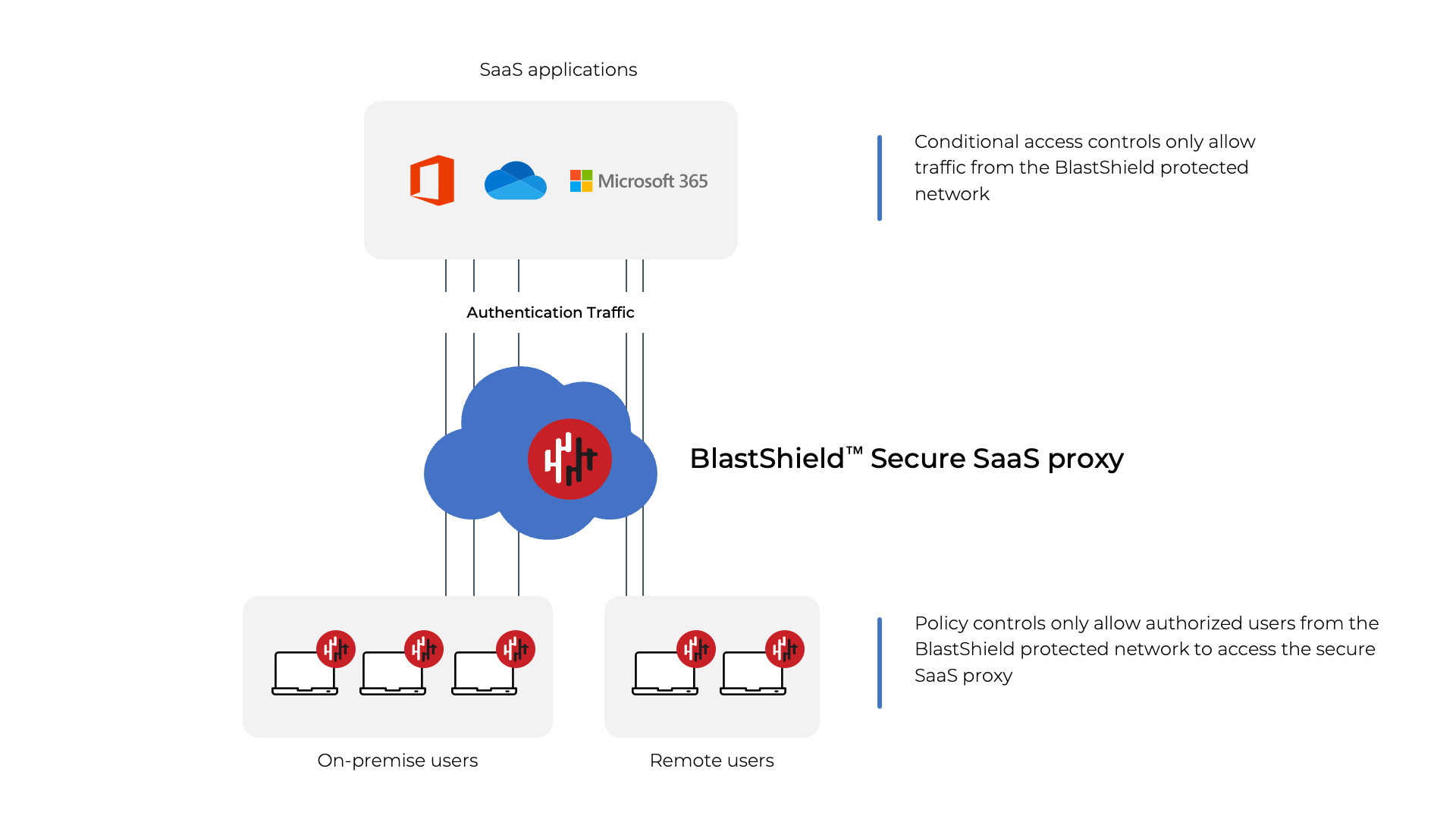
The benefits of using BlastShield™ to protect access to SaaS applications include:
Save time and money by using one solution to secure your public and private workloads.
Reduced complexity in the network with less time spend on administrative tasks.
Increased Security. All communications in the BlastShield™ network are encrypted and access to the network is protected with multi-factor authentication.
Functionality
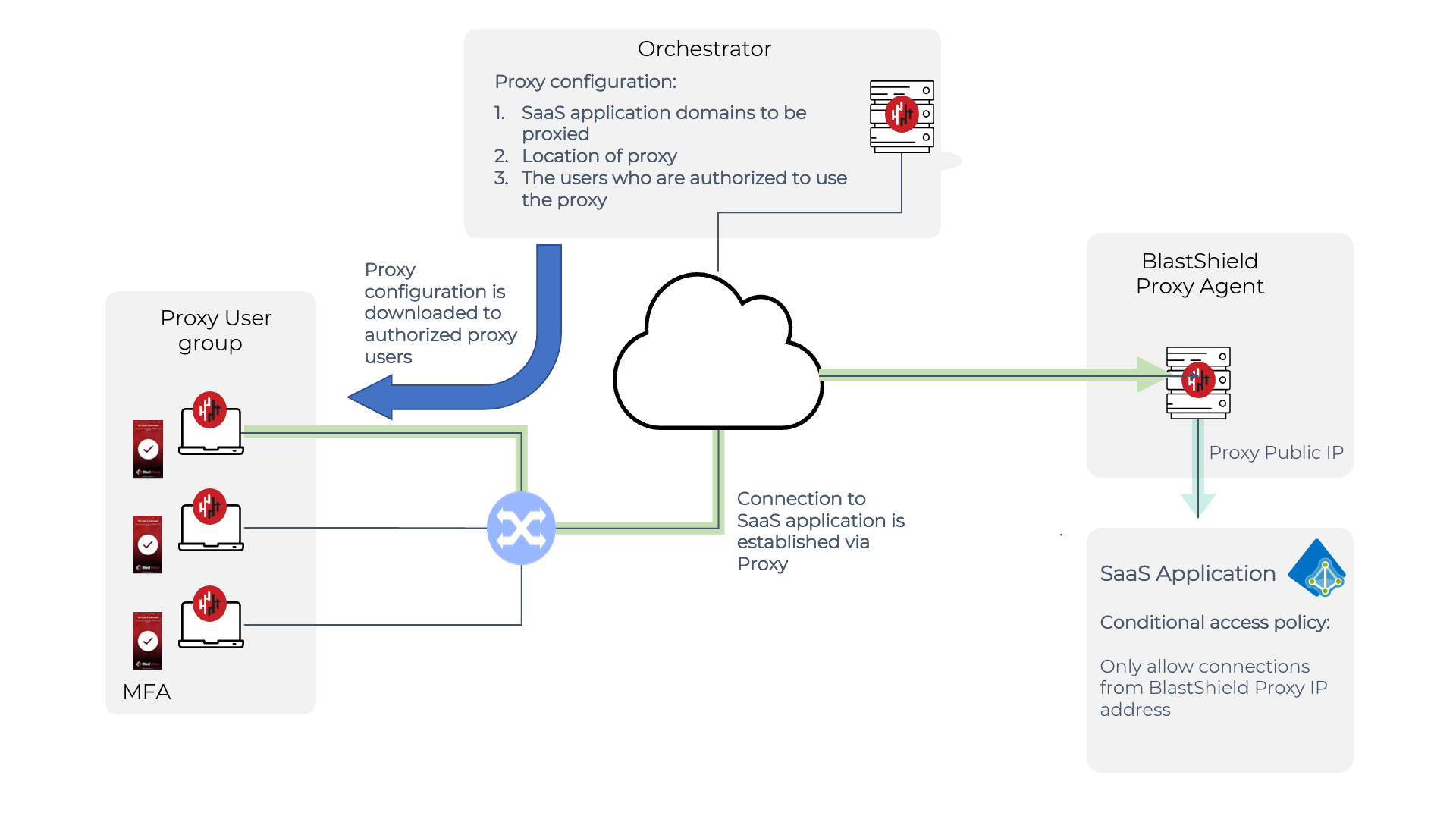
The Proxy Agent node can be a server, VM or cloud instance. It must have a BlastShield™ Agent installed on it.
Information about the domains to be proxied, the users who are authorized to use the Proxy Agent and the location of the Proxy Agent server are configured in the Orchestrator. Typically, only the authentication domains will be defined as the domains to be proxied, so that non-authentication traffic may connect on a peer-to-peer basis for optimum performance.
The proxy information is downloaded from the Orchestrator to authorized users.
When a user logs in to a nominated SaaS application, their browser will use the BlastShield Proxy Agent to establish the connection. Non-authentication traffic will be established on a direct peer-to-peer basis with the SaaS application..
The conditional access policy of the SasS application is configured to only allow inbound connections with a source IP address of the BlastShield™ Proxy Agent. This restricts the allowed logins to only authorized BlastShield™ users.
To learn how to configure the BlastShield™ SaaS Proxy Agent, please read this article: The BlastShield™ SaaS Proxy Agent
Extended access logging
Extended access logging gives you enhanced visibility of the user behaviour in your BlastShield™ network. When enabled, the enhanced access logging feature provides detailed logs of connections being made inside the protected network which can be exported to a third party syslog for viewing.
The extended access logging feature works by logging every connection event which matches a given BlastShield™ Policy so that you can monitor behavior at the granular policy level. Each connection log is date and time stamped and provides source + destination address and port information, along with the type of connection event, the user information and the data volume transferred.
Extended access logging is enabled in the Orchestrator at an individual policy level. To view the logs you must export them to a syslog server.
Click here for instructions on how to set up extended access logging and for detailed information on the log format.
Support for fully air-gapped deployments
BlastShield™ may be deployed as a fully air-gapped solution where there is no connectivity between the secured private network and the internet.
This is particularly useful where very high levels of security are required or local regulations mandate all components of the solution must be deployed on company infrastructure.
A fully air-gapped solution requires the BlastShield™ Orchestrator to be deployed on-premise and Users must authenticate using a FIDO2 compliant key.
The BlastShield™ Orchestrator provisions gateways, endpoints and remote users using invitation methodology. It manages the gateways, endpoints and remote users to modify or create policy and instances. The Orchestrator also provides real-time control of access, policy and segmentation. Only users with authorized privileges can access and use the Orchestrator.
To learn how to install the BlastShield™ Orchestrator on-premise, please read the following article: On premise installation of the Orchestrator (x86)
For a fully air-gapped deployment, Users must authenticate using the BlastShield™ client and a FIDO2 compliant key. To learn how to authenticate using a FIDO2 compliant key, please read the following article: Remote User Access - FIDO2 Key
An example fully air-gapped deployment architecture is shown below.
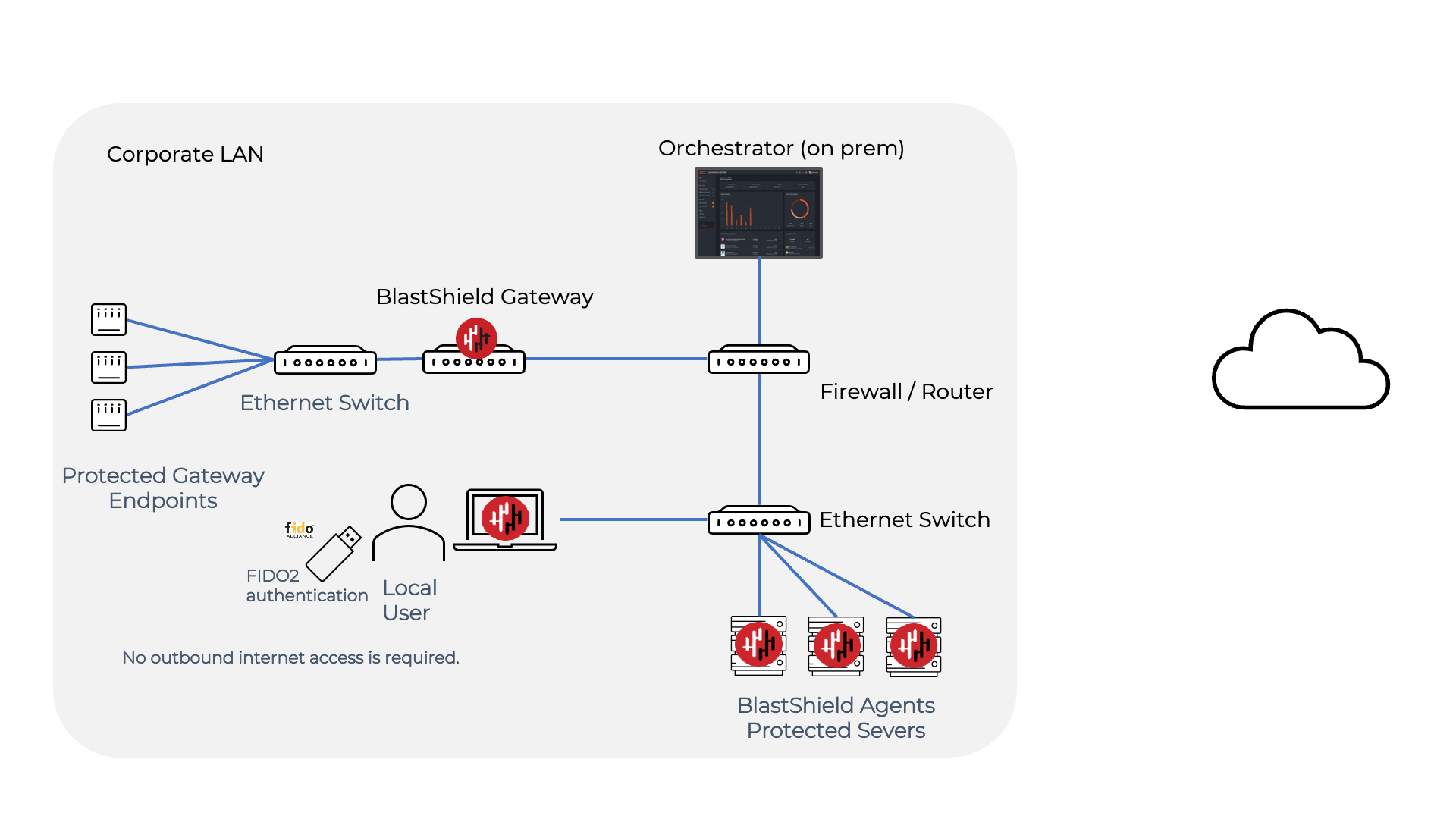
In this scenario, all the BlastShield™ nodes, including the Orchestrator, protected assets and users are air-gapped from the Internet. The Orchestrator is deployed on-premise and the Users authenticate using a combination of a FIDO2 compliant key and the BlastShield™ Client. No BlastShield traffic leaves the corporate LAN.
Enhanced Endpoint connectivity
The Enhanced support for Gateway Endpoint connectivity feature allows Endpoints behind an active BlastShield™ Gateway to create external connections to non-BlastShield™ nodes. The default condition for an Endpoint that is protected by an active BlastShield Gateway is that the Endpoint may only communicate to other nodes in the BlastShield™ network to which it is authorized. The Enhanced Endpoint connectivity feature allows such Endpoints to establish a connection to a non-BlastShield™ node that is outside of the protected network.
This feature is typically used if communications are required from a node or nodes in the BlastShield™ network to a node which is outside of the BlastShield™ network, for example if the protected Endpoint must periodically upload log files to a centralized data store.
To achieve this, the BlastShield™ Gateway provisions a default gateway IP address via DHCP on to the protected Endpoint. This gives the Endpoint a forwarding route out of the BlastShield™ network to non-BlastShield™ IP address ranges.. The BlastShield™ Gateway will NAT such outbound connections from the BlastShield™ IP address range to non-BlastShield™ IP address ranges, allowing a connection to be established from the protected Endpoint to the non-Blastshield™ node.
The following diagram shows how the enhanced connectivity works. An Active Gateway (configured to use 'MAC address' as the addressing mode) is shown protecting a server Endpoint. This Endpoint has a protected IP address on the BlastShield network of 172.16.0.2 and in the default Endpoint configuration it would be isolated from non-BlastShield™ nodes due to the layer 2 isolation provided by the Gateway. With the Enhanced Endpoint Connectivity mode enabled, the protected endpoint may now open a connection to the non-BlastShield™ endpoint with IP 10.100.10.10.
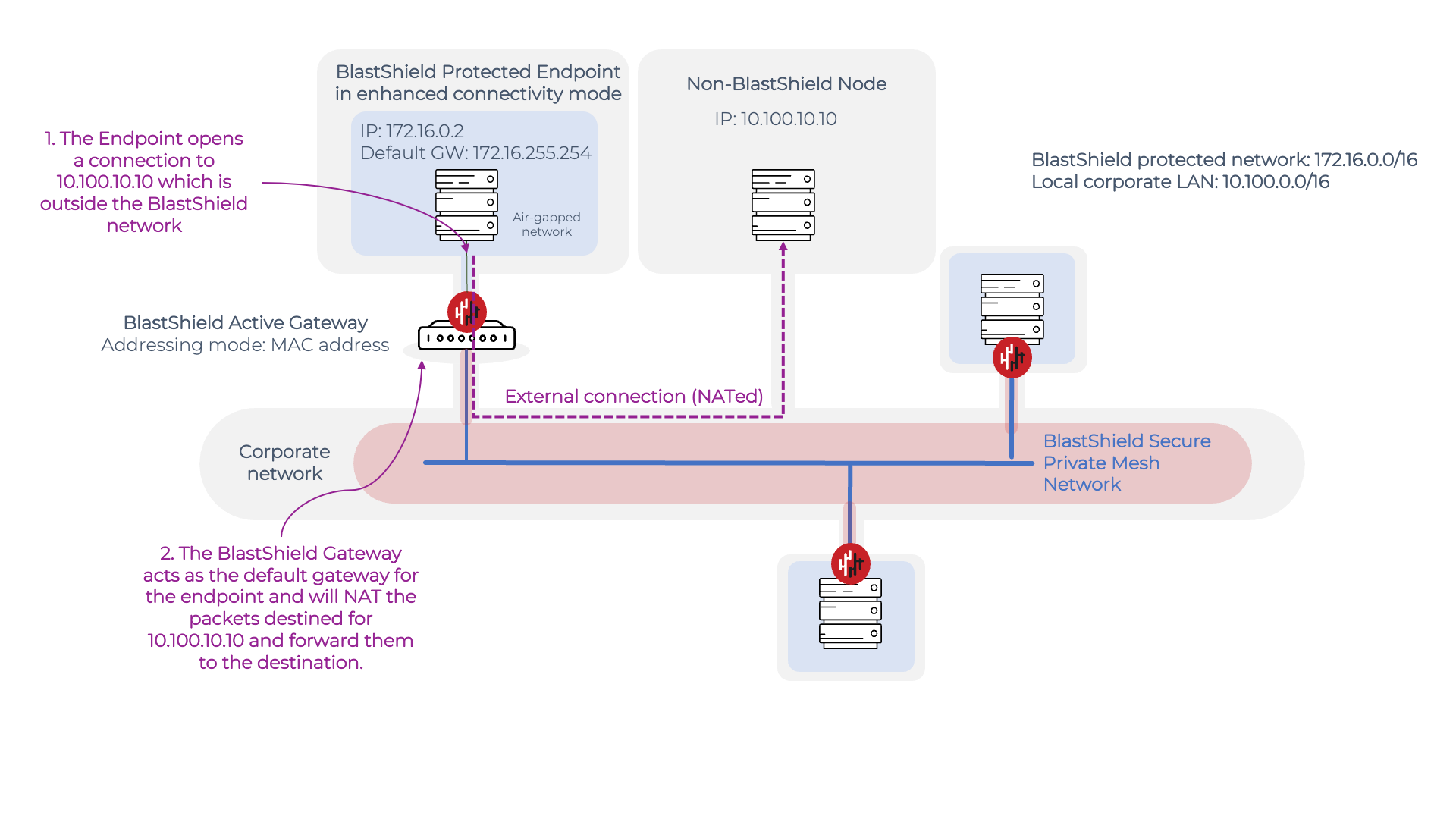
The enhanced connectivity works as follows:
When it boots up, the Endpoint requests an IP address from the BlastsShield™ Gateway.
The Gateway responds by allocating an IP address from the BlastShield™ network prefix to the Endpoint via DHCP. Because the Enhanced Endpoint Connectivity feature is enabled, the BlastShield™ Gateway also allocates a default gateway address in the DHCP offer.
When the Endpoint establishes a connection to 10.100.10.10 which is outside the BlastShield™ network, it uses the default gateway address for the connection.
The BlastShield™ Gateway receives packets destined for the default gateway address and will NAT these packets and then forward them to the 10.100.10.10 destination.
To learn how to configure the Enhanced support for Gateway Endpoint connectivity, please read the following article: Configure Enhanced Gateway Endpoint Connectivity
Upgrade instructions
Upgrade your Desktop Client.
See the following page for details. Update the BlastShield™ Desktop Client
Upgrade the firmware of the BlastShield™ Orchestrator.
See the following page for details.Upgrade the Orchestrator firmware
Upgrade the firmware of the connected BlastShield™ Gateways.
See the following page for details.Upgrade the Gateway
Upgrade your BlastShield™ Agents.
See the following pages for details.Upgrade an Agent from the host or Upgrade the Agent from the Orchestrator