Configure Okta as an external identity provider and use the BlastShield™ Authenticator for user authentication
In this configuration, users and user groups will be provisioned by the identity provider and the user authentication will use the BlastShield™ Mobile Authenticator app.
BlastShield™ is SCIM 2.0 enabled and supports integration with identity providers such as Okta, Azure AD and One Identity. SCIM support allows user accounts to be automatically created in BlastShield™ when new user accounts are assigned to the SCIM application in the IdP. User account status and their information are automatically updated in BlastShield™ based on updates in the IdP. BlastShield supports OIDC (OpenID Connect) to authenticate the SSO of the IdP for the user registration with the Orchestrator.
Your Orchestrator must have an SSO portal hostname configured for your network. Please contact support@blastwave.com to get one configured.
You must have administrative read/write access to the BlastShield™ Orchestrator and to the Okta configuration portal.
Users must have a mobile device with the BlastShield™ Mobile Authenricator app installed for registration and authentication. You can download it from here: Mobile Authenticator download links
Users must have the BlastShield™ Desktop Client installed on their workstation. You can download it from here: Client download links
https://auth.blastwave.io outbound.
Outbound UDP ports to all destinations.
If you use DNS over HTTPS, ensure it is configured in your OS and not in your browser to allow the BlastShield Client to use its associated DNS server.
Ensure that the timezone is correctly set on your computer for your location and that the clock is set accurately.
Set up OpenID Authentication.
Configure the SCIM Provisioning.
Register the user with the Mobile Authenticator app.
Connect the BlastShield™ network.
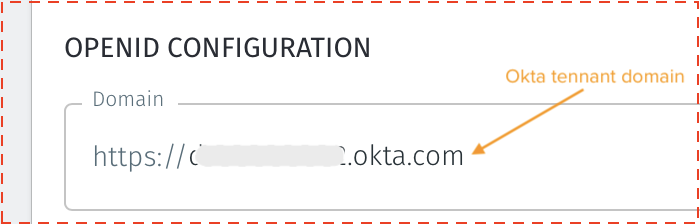
Find your Okta domain and copy it. To find your Okta URL (also called an Okta domain), sign in to your Okta organization with your administrator account, and look for the Okta domain in the global header located in the upper-right corner of the dashboard.
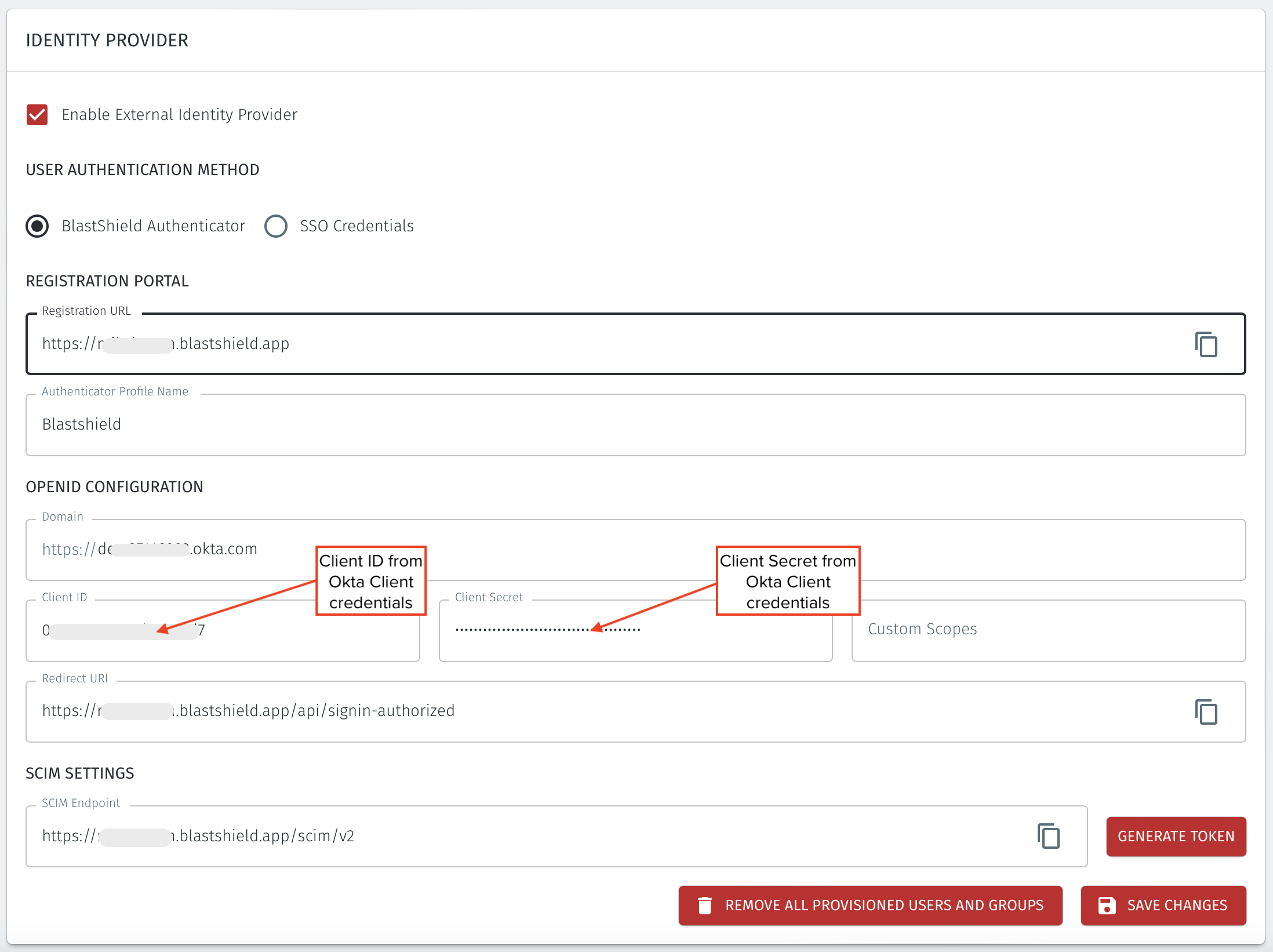
Open the BlastShield™ Orchestrator and from the settings menu on the left, go to the “Identity Provider” settings page..
Click on the Enable External Identity Provider checkbox.
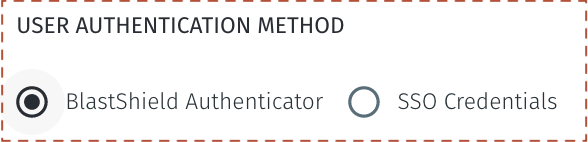
Under USER AUTHENTICATION METHOD, select the option for BlastShield Authenticator:
In the OpenID configuration section, enter your Okta tenant domain (i.e mycorporation.okta.com) as the “Domain”. Make sure to leave out any trailing slashes.
In Okta, click “Create App Integration” and select “OIDC - OpenID Connect” followed by “Web Application” and click “Next”.

Name the App integration “BlastShield OIDC”.
Find the "Redirect URI" from the OpenID configuration in the BlastShield™ Orchestrator. This is in the format https://<your-domain>.blastshield.app/api/signin-authorized and is located as shown here:
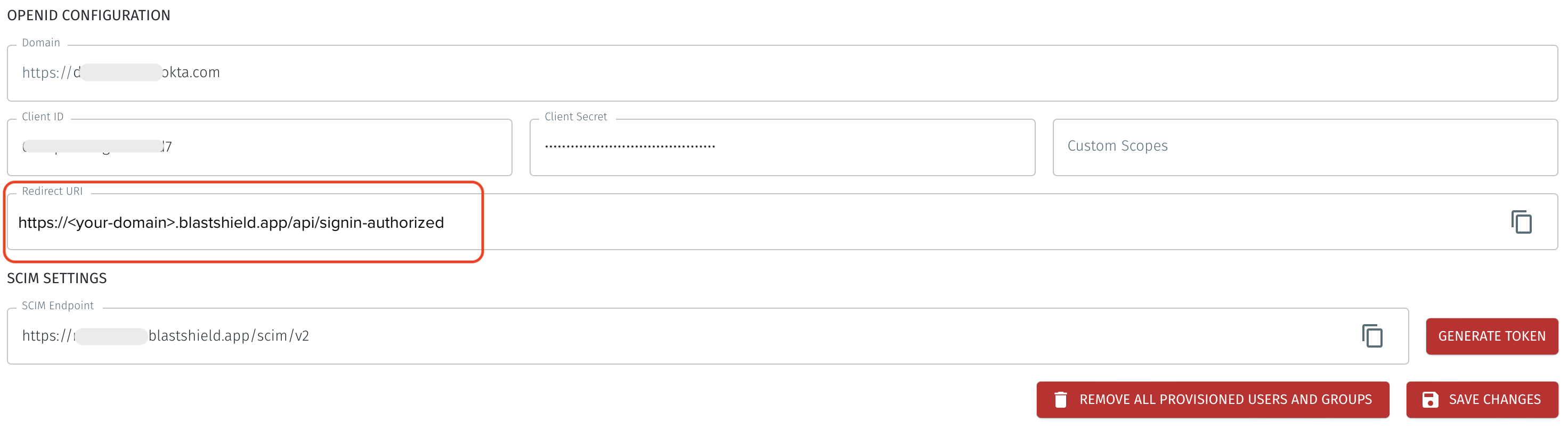
Copy the “Redirect URI” from the BlastShield™ Orchestrator and paste it in as the “Sign-in redirect URI” in Okta. Remove any default “Sign-out redirect URIs”.
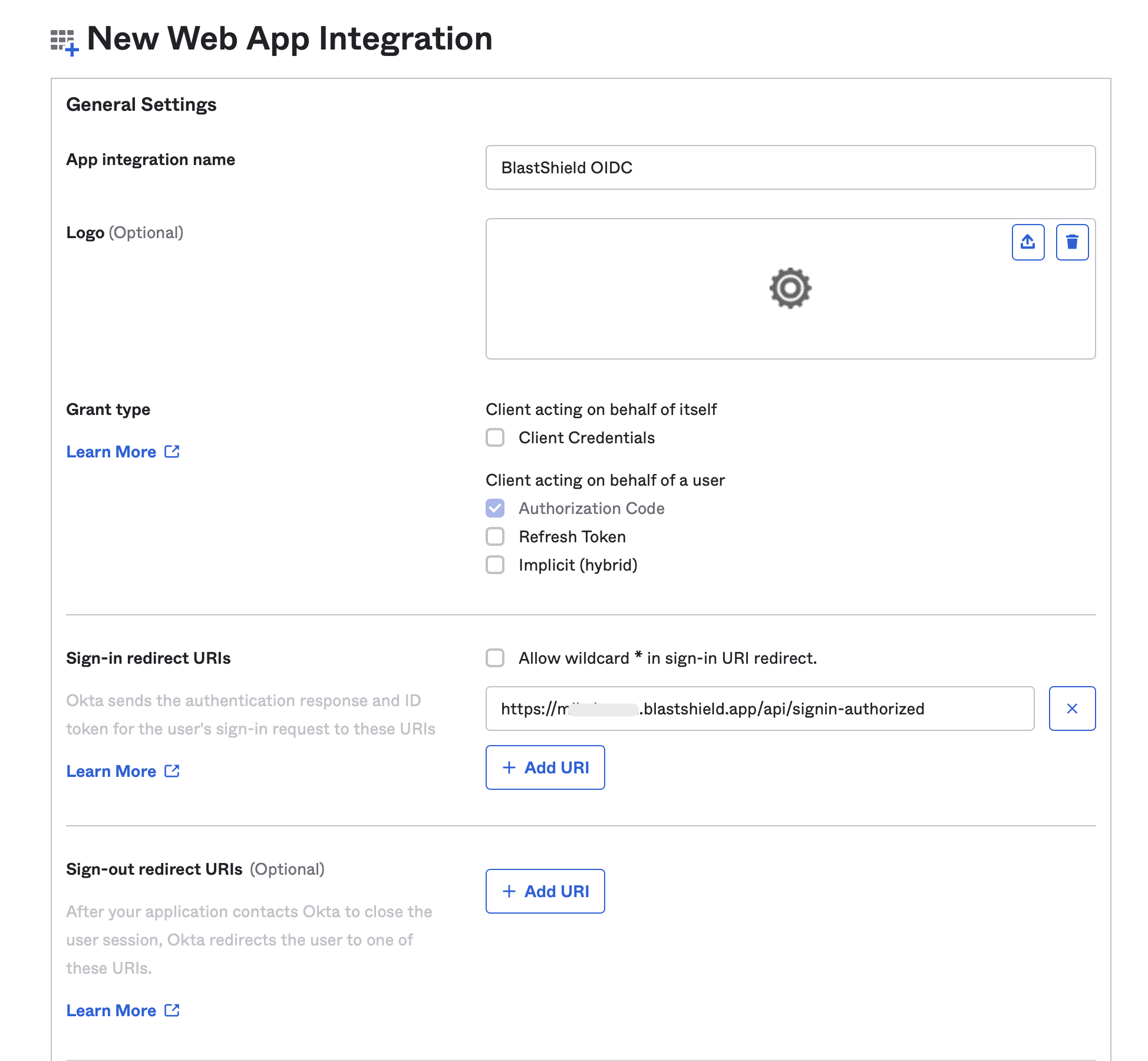
Under “Assignments” select your preferred option and click “Save”.
Copy the “Client ID” and the generated “Client Secret” from Okta and paste it into the corresponding text fields in BlastShield.
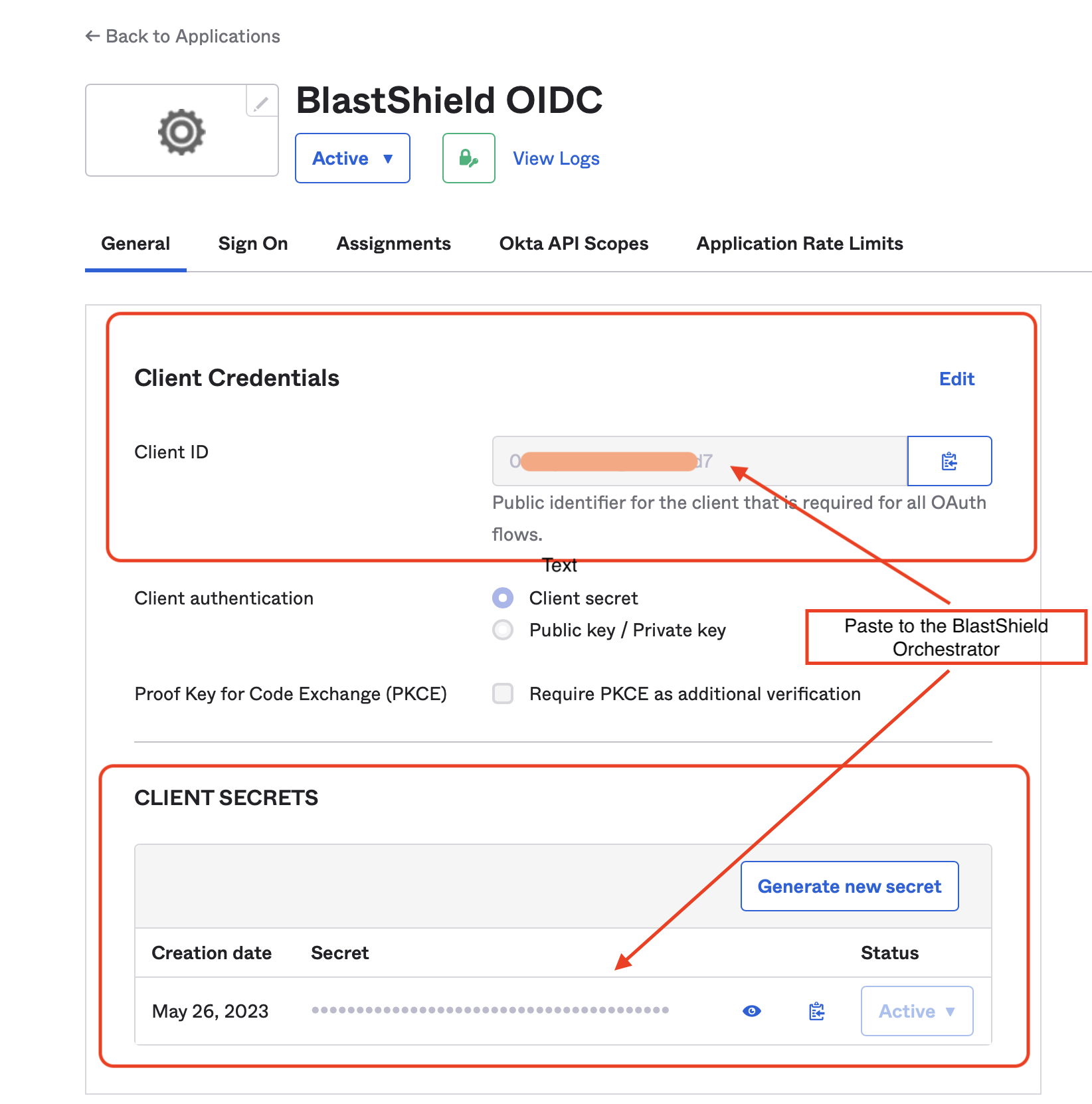
Click “Back to Applications”.
In Okta, click “Create App Integration” and select “SWA - Secure Web Authentication” and click “Next”.

Enter
BlastShield SCIMas the “App name” and copy the “REGISTRATION PORTAL > Registration URL” from the BlastShield Orchestrator and enter it as the “App’s login page URL” in Okta and click “Finish”.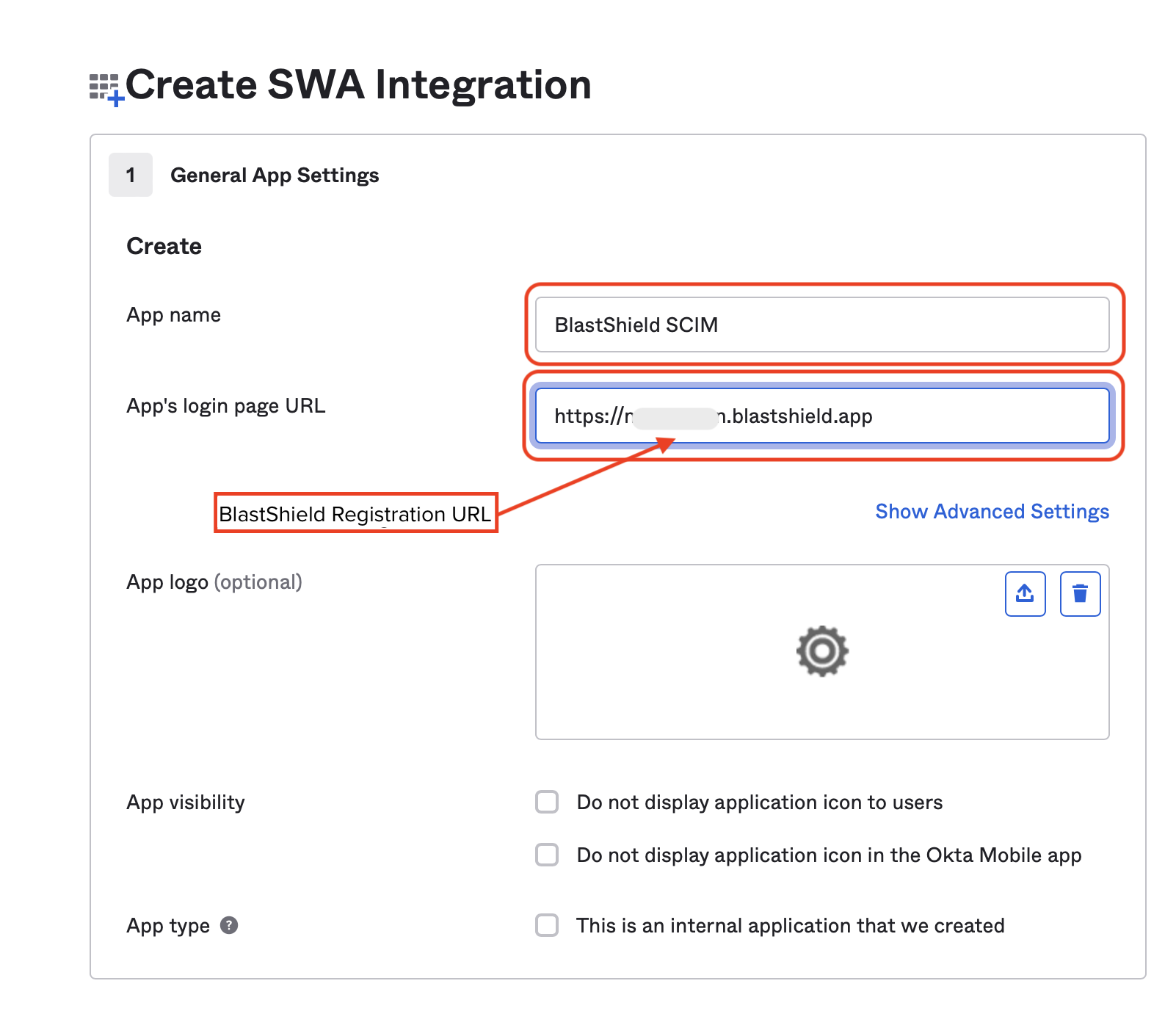
Click on the “General” tab and select “Edit” in the “App settings” box. Select “Enable SCIM provisioning” and click “Save”.
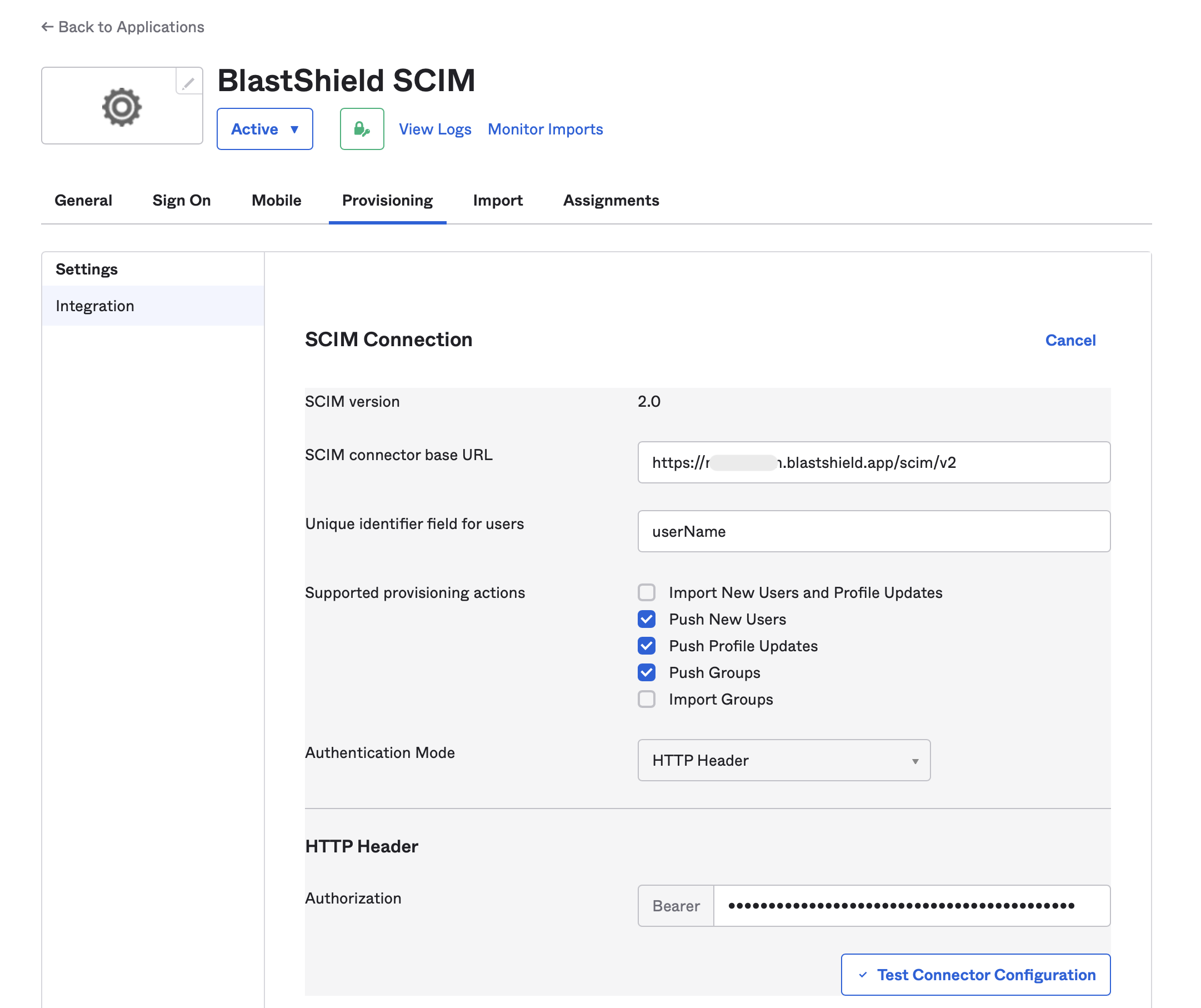
Click on the “Provisioning” tab and select “Edit” next to “SCIM Connection”.
Copy the “SCIM Endpoint” from BlastShield and enter it as the “SCIM connector base URL” in Okta.
Enter
userNameas the “Unique identifier field for users”.Under “Supported provisioning actions”, check “Push New Users”, “Push Profile Updates” and “Push Groups”.
Select “HTTP Header” as the “Authentication Mode”.
In BlastShield, click the “Generate Token” button and copy the token to the clipboard. Click “Save Changes” before going back to Okta.
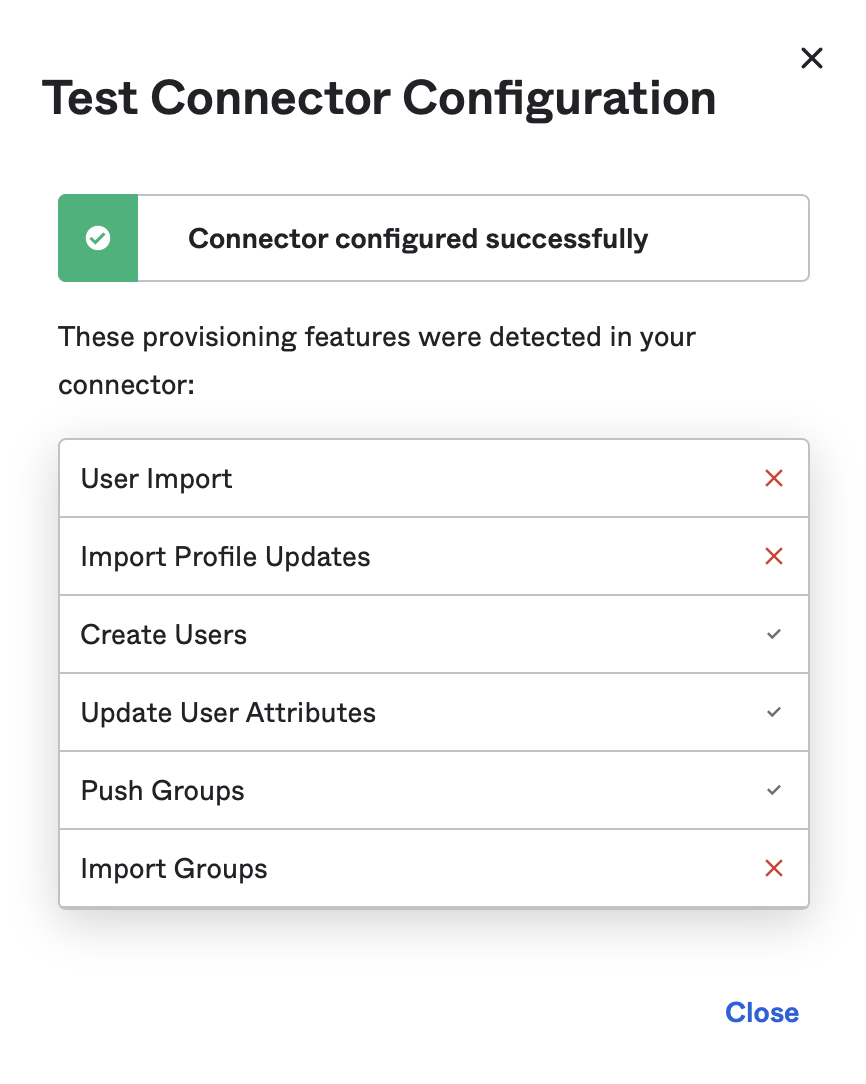
Paste the copied token into “Authorization” field and click on “Test Connector Configuration”.
Make sure that the test results show “Connector configured successfully”, then click “Save”.
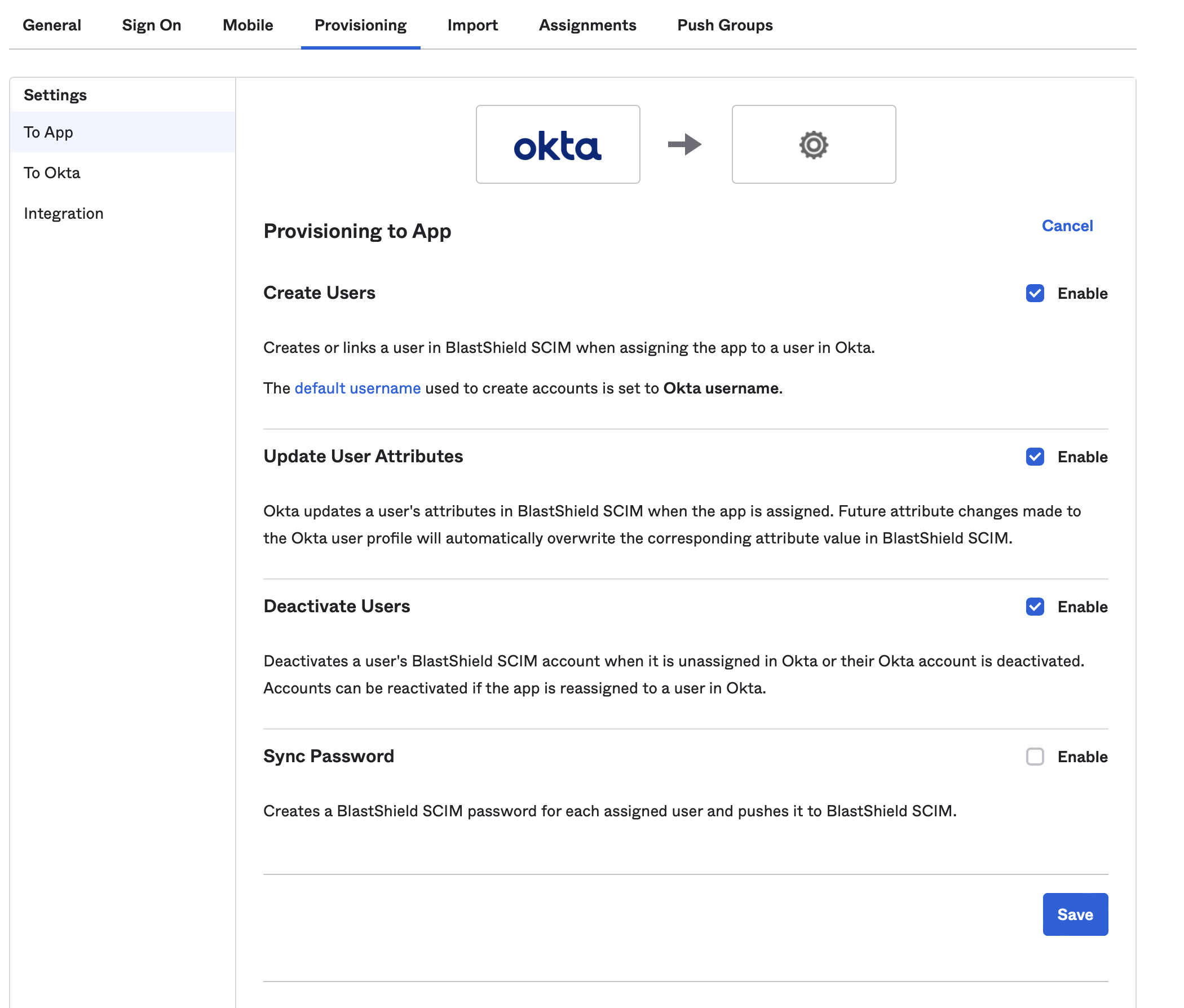
Click “Edit” next to “Provisioning to App” and enable “Create Users”, “Update User Attributes” and “Deactivate Users”, then click “Save”.
Click on the “Assignments” tab and assign the users and/or groups that you want to give access to your BlastShield Network.
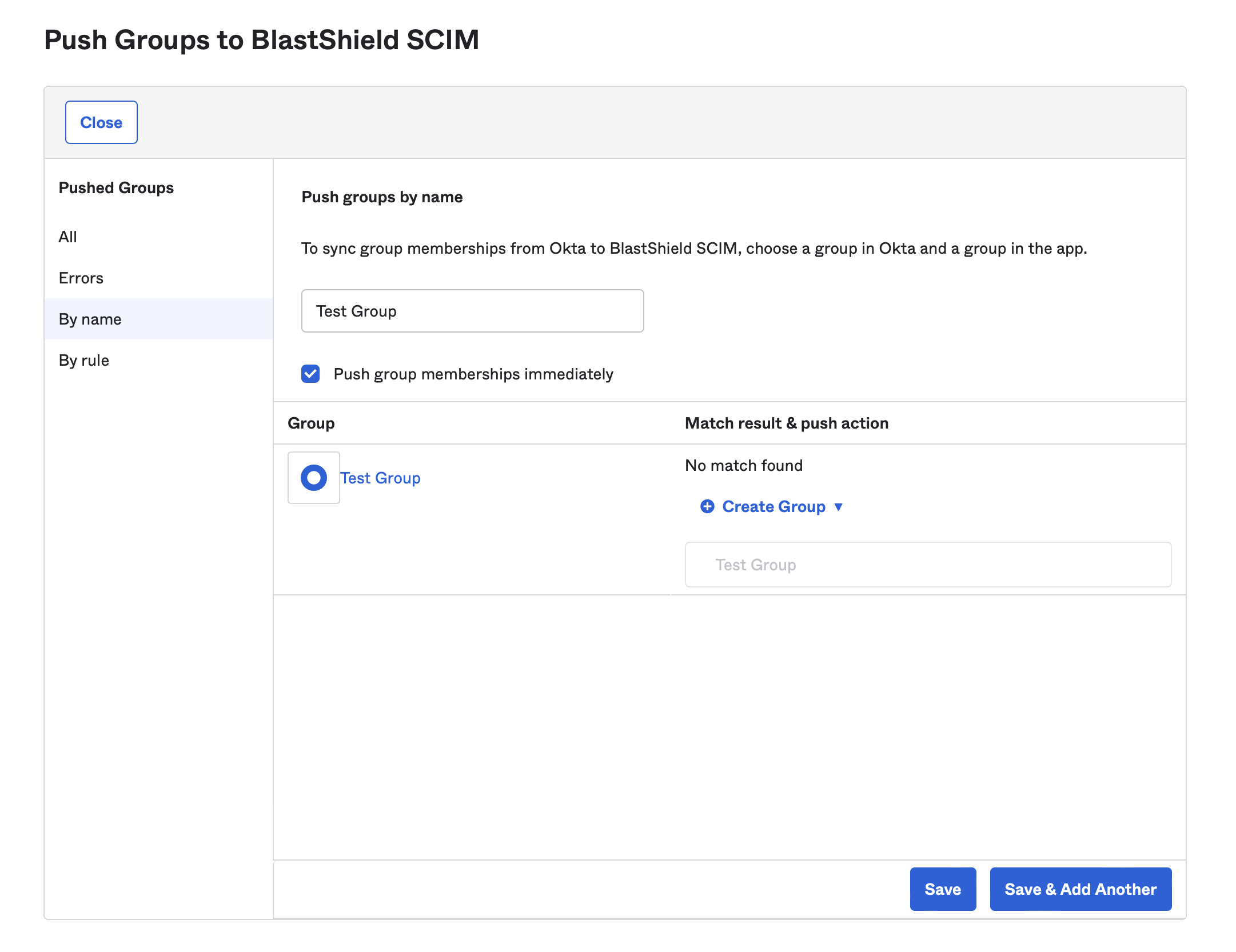
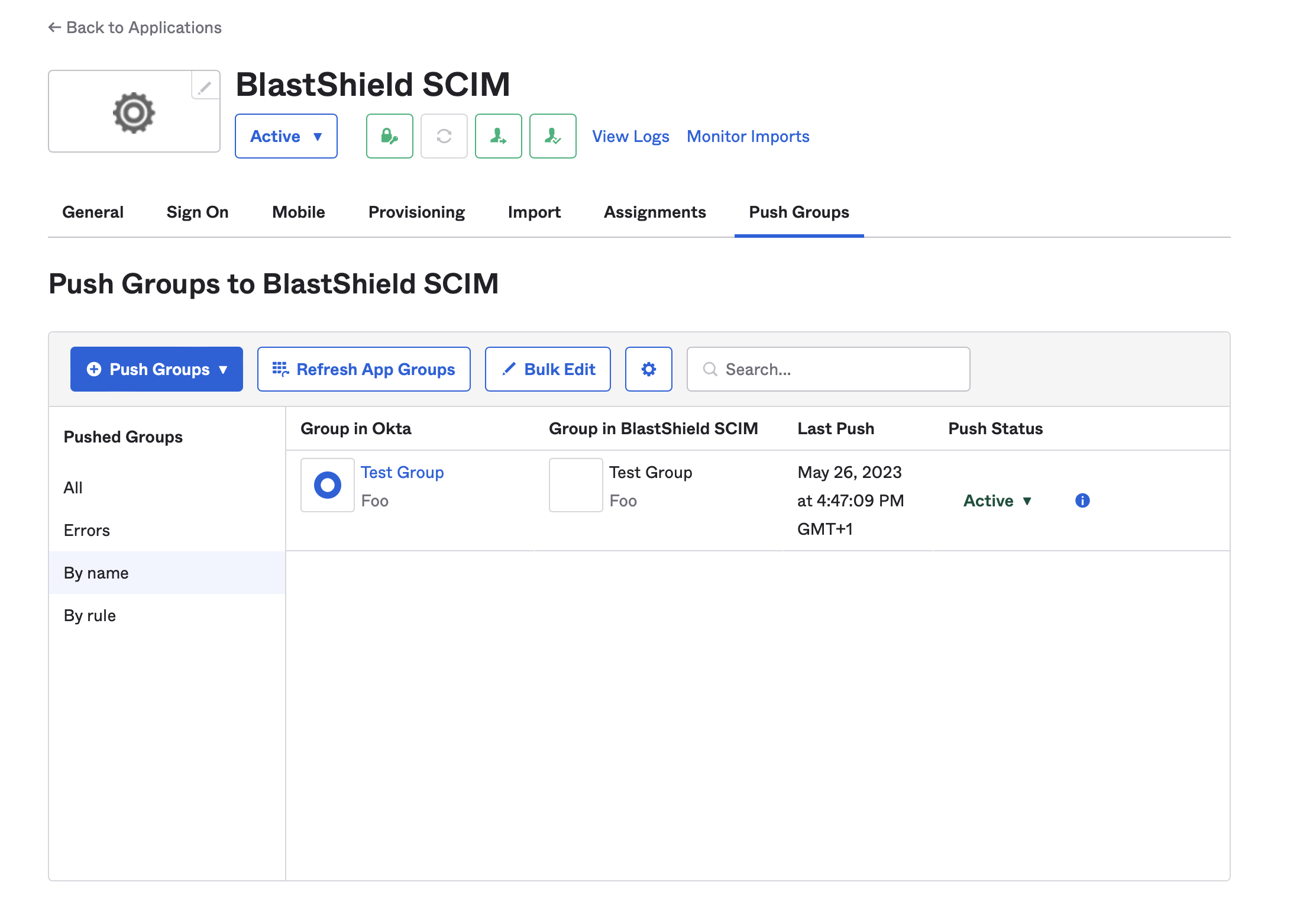
Optionally click on the “Push Groups” tab and push the groups that you want to import into BlastShield.
Note
When this configuration is completed, users and groups which are assigned to the BlastShield™ application in Okta will be automatically provisioned into the BlastShield™ Orchestrator, and will be available to use in BlastShield™ policies. It is not possible to modify the provisioned groups from the Orchestrator, but you can add a provisioned user to Blastshield™ created groups.
Register a new user
To learn how to register a new user, please follow the link: Register a new user created by an external identity provider
Once the user has registered then that user will be able to log into BlastShield™ using only the BlastShield™ MFA as explained below. It would only required to login to the BlastShield™ web portal if the user needs to reset their registration in the case of a lost or changed mobile device.
Connect to BlastShield™ using the Desktop Client
To learn how to register a new user, please follow the link: Connect to BlastShield™ using the Desktop Client