VMware passive Gateway installation - source + destination NAT mode
This article explains how to install the BlastShield™ Gateway OVA in VMware ESXi where the Gateway is configured with IP Address (Source+Destination NAT) addressing mode to work as an passive Gateway.
A passive Gateway deployed on VMware can be used to secure remote access to external OT systems, IoT devices and networking appliances.
Using source + destination NAT mode will allow you to connect external endpoints to the Gateway without modifying the routing of the endpoints.
Endpoints will not be able to initiate connections out over the BlastShield™ network.
The secure remote access uses BlastShield's zero-trust peer-to-peer encrypted network with micro segmentation, where all users must first authenticate using BlastShield's MFA before they can connect.
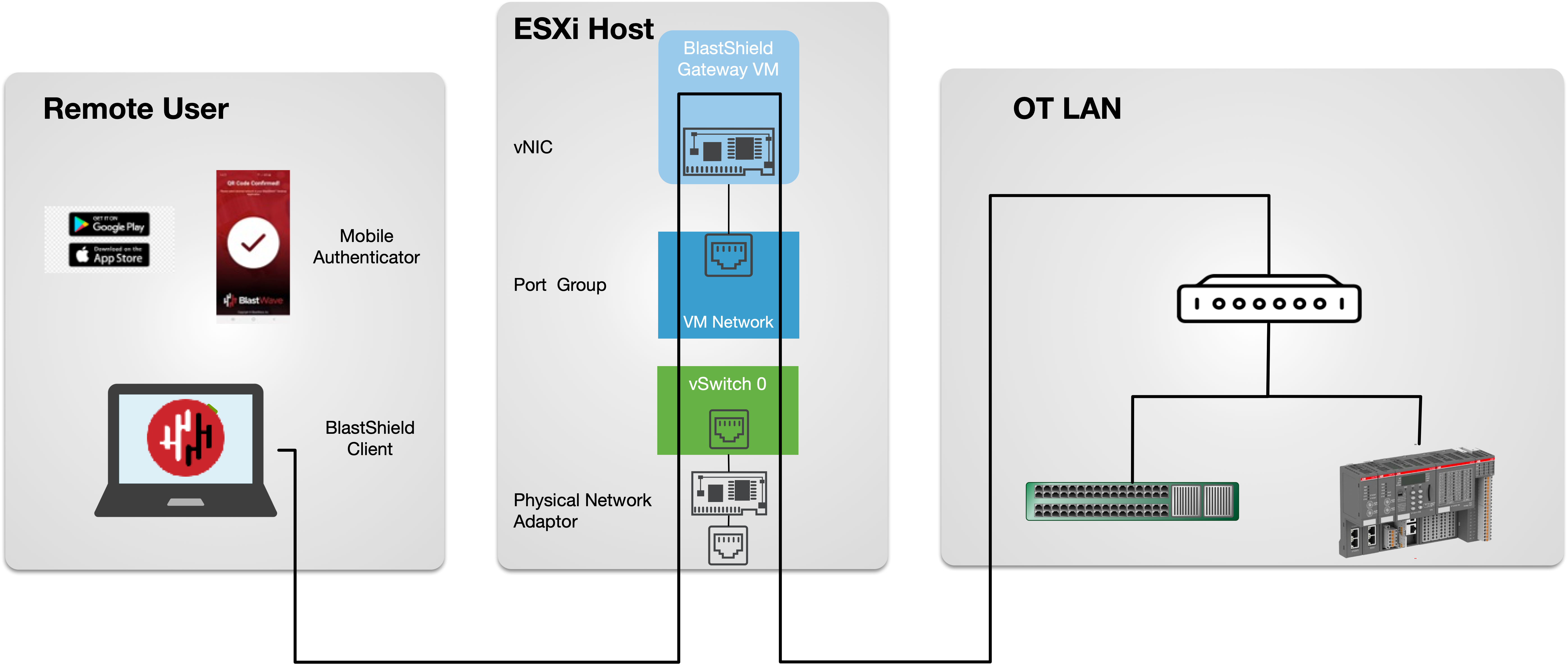 |
This figure shows a Passive Gateway providing secure remote access to OT and networking assets.
Prerequisites
A VMware ESXi7 hypervisor with admin access.
A BlastShield™ Orchestrator with administrator access..
The ESXi hypervisor requires at least one physical NIC which is connected to the internet.
The BlastShield™ Gateway requires outbound UDP ports to all required destinations.
You will require a copy of the Gateway OVA file. It can be downloaded from here.
By default, the gateway expects to receive an IP address via DHCP. Manual assignment is also supported during the installation process.
Add a new Gateway in the Orchestrator.
Create the Gateway in the Orchestrator and copy the invitation information for use later when you install the Gateway OVA.
Download the Gateway OVA file.
Install the Gateway OVA file on the ESXi client.
Using the VMWare ESXi new virtual machine installer, install the Gateway OVA on the ESXi hypervisor and register it to the BlastShield™ Network using the invitation information from Step 1.
Add Endpoints to the Gateway.
For each of the devices that you want to securely access via the BlastShield™ Gateway, you must create a corresponding endpoint for it on the Gateway.
Configure an access policy and microsegmentation.
BlastShield™ is a zero trust solution and without a policy to authorize access, users or other nodes will not be allowed to connect to a protected endpoint. To enable access, you define one or more groups of endpoints and bind the endpoint group(s) to a defined group or groups of users with a policy. The groups provide microsegmentation of the endpoints and users, and the policy defines the access authorization.
Connect to the Orchestrator and select Gateways from the left Menu.
Select Add New Gateway.
Enter a name for the new Gateway.
Select Addressing Mode for the Gateway to be IP Address (Source+Destination NAT).
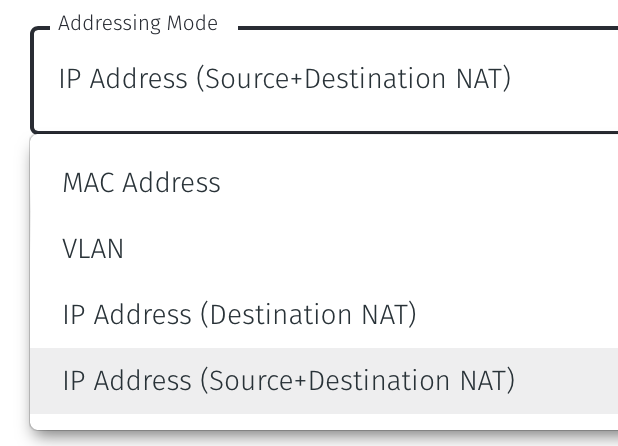
Select Save and Download Invitation. You can chose to either download the invitation file or copy it to the clipboard. Keep the invitation data as you will need it in a later step.
Download the Gateway OVA file from here and keep it available so that you can upload it to your ESXi server.
Using the VMWare ESXi new virtual machine installer, the Invitation (.bsi) file generated in step 1 and the OVA file you downloaded in step 2 you will install the software on your ESXi hypervisor and register it to the BlastShield™ Network. The process is explained below.
Install the BlastShield Gateway™ OVA file on the ESXi client.
Using the VMWare ESXi new virtual machine installer, the Invitation (.bsi) file generated in step 1 and the OVA file you downloaded in step 2 you will install the software on your ESXi hypervisor and bind it to the BlastShield™ Network. Below are the steps for this process.
From the ESXi host, go to Virtual Machines > Create/Register VM > Create a virtual machine from an OVF/OVA file
Give the new Gateway a name and select the BlastShield™ OVA file which you downloaded in the previous step.
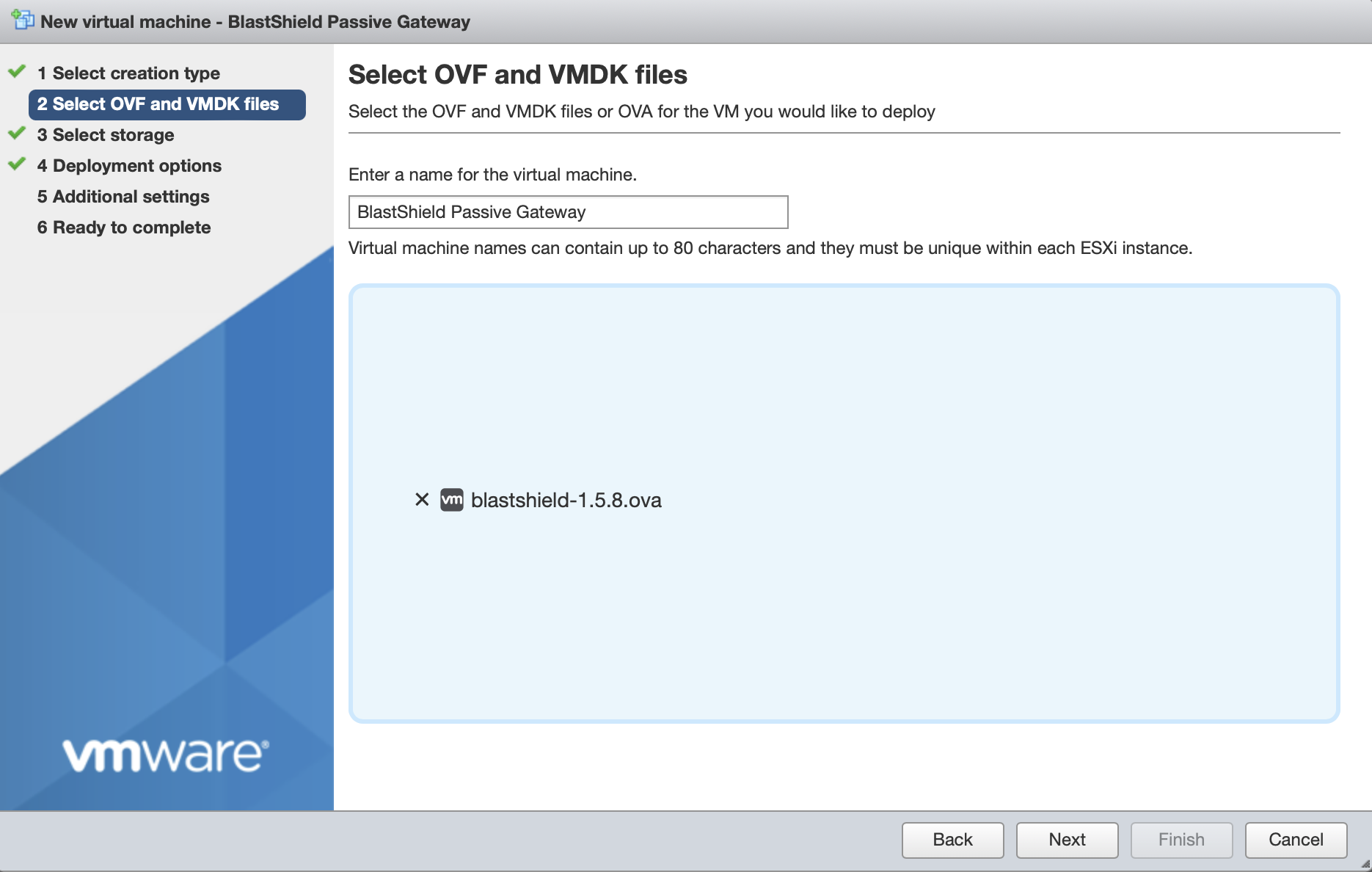
Leave the default datastore option.
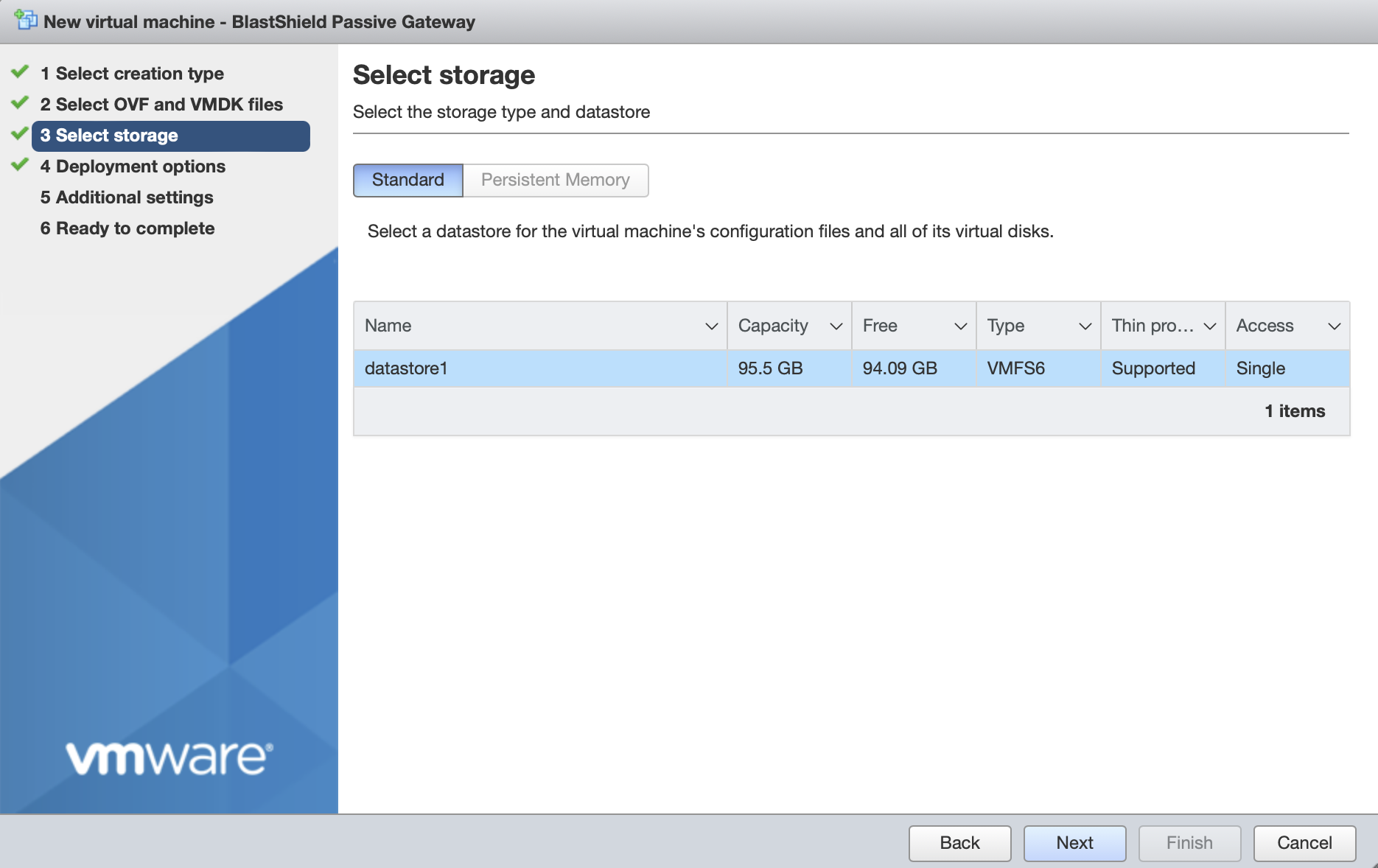
Deployment options
'Network mappings' should use the default "VM Network" port group for both the Public and Protected network settings on the BlastShield™ Gateway as shown here.
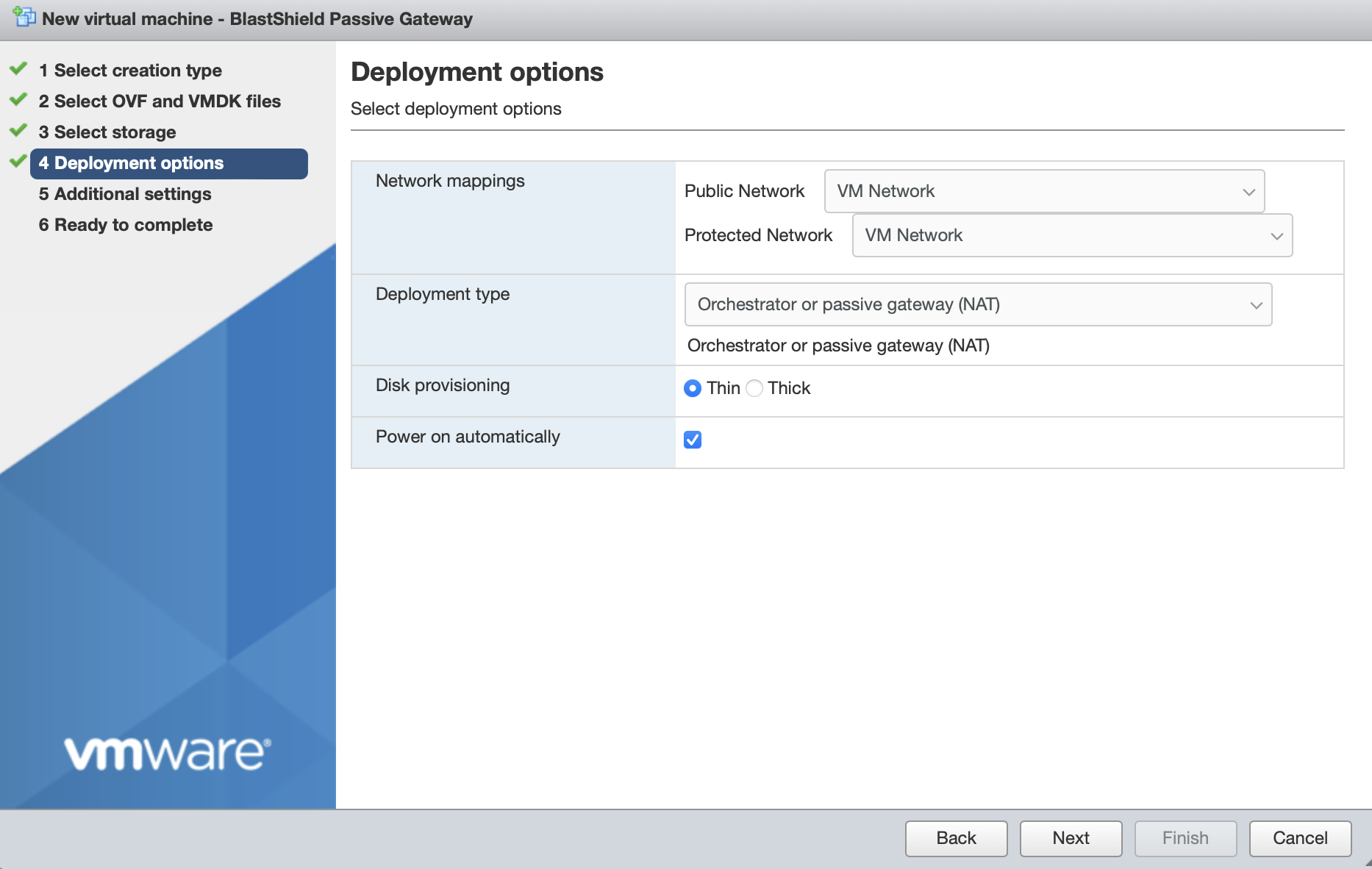
Deployment type should be set to Orchestrator or passive gateway (NAT).
Disk provisioning' and 'Power on automatically' should use the default settings.
In Additional Settings, add the contents of the bsi file.
Paste the contents of the Gateway BSI file (from Step 1, above) into the Invitation contents box.
For IP addressing, the default option is that the Gateway will use DHCP. If you are setting a manually assigned IP address, default gateway and DNS, then enter them here . Leaving the boxes blank here will use DHCP.
Click next, then click finish to add the new Gateway virtual machine.

Then click 'Finish' to complete the configuration and launch the VM.

You can verify the Gateway has started by watching the console output in the hypervisor. when the Gateway is up, then the status in the Orchestrator will indicate 'online' as shown in the image below.

Troubleshooting if your Gateway status does not come Online
Ensure you have pasted the contents of the bsi file from the Orchestrator into the Additional settings step of the Create/Register VM procedure when you install the Gateway OVA on the hypervisor.
If your hypervisor environment is not running a DHCP server, make sure you have manually configured an IP address in the Network Configuration section of the Additional settings step of the Create/Register VM procedure on the hypervisor. You can manually enter an IP address, default gateway and DNS server in the Network Configuration.
Ensure there is internet access on the hypervisor, because the Gateway will attempt to connect to the Orchestrator when it boots. Addtionally, make sure that your firewall is allowing outbound access. See the list of required destinations below.
Outbound UDP ports to all destinations.
For each of the devices that you want to securely access via the BlastShield™ Gateway, you must create a corresponding Endpoint for it on the Gateway.
Follow this procedure to learn how to create an Endpoint on the Gateway.
In the Orchestrator, select the AWS Gateway and click on the Endpoints tab.
Click the 'Add New Endpoint' button and click on the 'Endpoint Enabled' button.
Enter a name for the Endpoint in the Name field.
In the DNS Hostname field, enter a hostname.
In the Destination field, enter the device's Private IPv4 address or hostname.
Click on 'Save Changes'.
The status of the Endpoint will show as 'Online'.

About Groups
Groups allow you to micro-segment users and endpoints. A group is a logical collection of endpoints and/or users that are grouped together. Groups are connected via policies, which form the foundation for BlastShield access control and segmentation management.
Any combination of endpoints and/or users can be grouped together.
There is no limit to the number of endpoints and/or users that can be in a group.
Endpoints and users can be in one or multiple groups simultaneously.
Groups are linked together via policies to provide access between endpoints.
By default, endpoints/users cannot access or have visibility to other endpoints/users unless they are granted access via a policy
About Policies
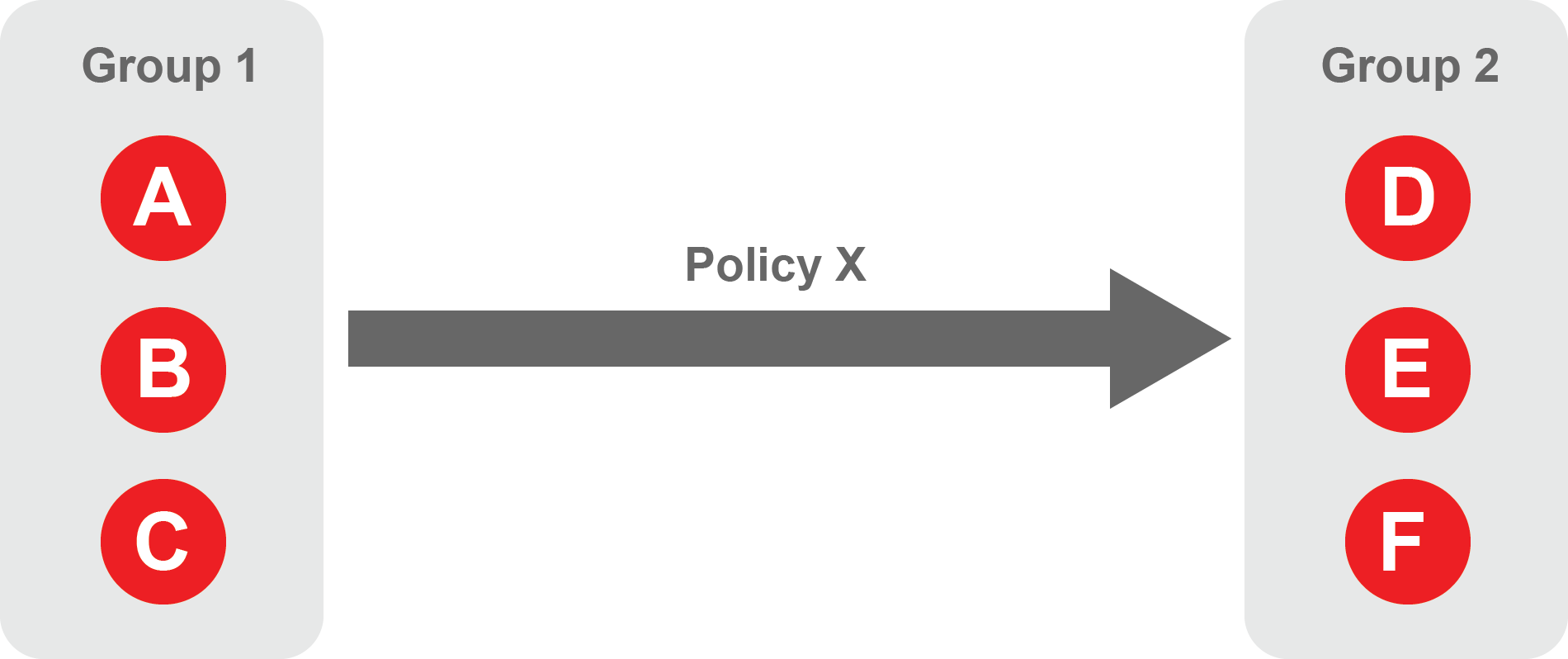
A policy defines how groups can interact. Groups are connected via policies, which form the foundation for BlastShield access control and segmentation management.
Each policy will have two sets of groups - "From" and "To".
The "From" set is one or more source groups.
The "To" set is one or more destination groups.
There is no limit to the number of groups in a given policy.
"From" Groups will have access to "To" Groups within the policy.
"To" Groups will not have access to "From" Groups within the policy.
Groups can be in one or multiple policies simultaneously.
 |
Create Groups
From the Orchestrator, select "Groups" from the left menu.
Select "Add New Group" from the Group List.
Enter a name for the new Group.
To add members to the new group, click the "Add Members" button.
If you adding users to the group then select the desired Users which you want to be associated with the Group from the "Users" box.
If you are adding Agents to the group then select the desired Agents which you want to be associated with the Group from the "Agents" box.
If you are adding Gateway Endpoints then select the desired Endpoints from the "Endpoints" box.
Alternatively, you can leave the members list empty and add/modify new members later.
Click "Add Members" to save the members.
Click "Save" to save the new group.
Repeat, if required, to ensure you have one group for your endpoints and one group for your users, which is the minimum you will need in order to define the access policy.
Please refer to the following video, which is an example of creating one group for your users and one group for Host Agents.
Create a Policy to link your Groups
Note
Users and Agents must be a member of a group for them to be used in a policy.
Select "Policies" from the left menu.
Select "Add New Policy" from the Policy List.
Enter a name for the new Policy.
Select desired "From" Groups to be associated with the new Policy.
Select desired "To" Groups to be associated with the new Policy.
Save the new Policy.
Policies are directional, so that you can control the direction in which connections may be initiated. Typically for remote access use-cases your policy would be from the "user group" to the "server group" so that users may start connections to the servers, but servers cannot start connections to users. You can create bi-directional permissions by using two policies.
The following video shows an example of creating an access Policy between a group of remote workers and a group of servers. The policy gives the remote workers authorisation to access the server group.