Firmware Version 1.4 Release Notes
Release Date: 6th May 2022
Firmware release 1.4
Release content
New Features
Added options to copy invitation or self-contained install command to clipboard when adding a new agent or gateway.
Added single vNIC deployment option to OVA appliance.
Support for external identity managers with SCIM provisioning and OpenID Connect.
Support for running gateways in Microsoft Azure.
Bug Fixes
Fixed a buffer leak in agents and clients which could potentially lead to a situation where the agent/client would fail to connect to the orchestrator with a "Failed to connect to orchestrator: Connection failed" message in the log.
Fixed compatibility with Safari and the new "Copy invitation to clipboard" actions.
Fixed fetching of the certificate for the SSO portal.
Components to be upgraded
New firmware is available for the following applications.
BlastShield™ orchestrator.
BlastShield™ gateway.
BlastShield™ host agent.
BlastShield™ desktop client.
Feature Descriptions
Support for external identity managers
From release 1.4, BlastShield™ is SCIM 2.0 enabled and supports integration with identity providers such as Okta, Azure AD and One Identity.
SCIM support allows user accounts to be automatically created in BlastShield™ when new user accounts are assigned to the SCIM application in the IdP. User account status and their information are automatically updated in BlastShield™ based on updates in the IdP. BlastShield supports OpenID Connect to authenticate the SSO of the IdP for the user registration with the orchestrator.
Once registered, Users will authenticate via MFA with the BlastShield™ mobile authenticator app and the desktop client.
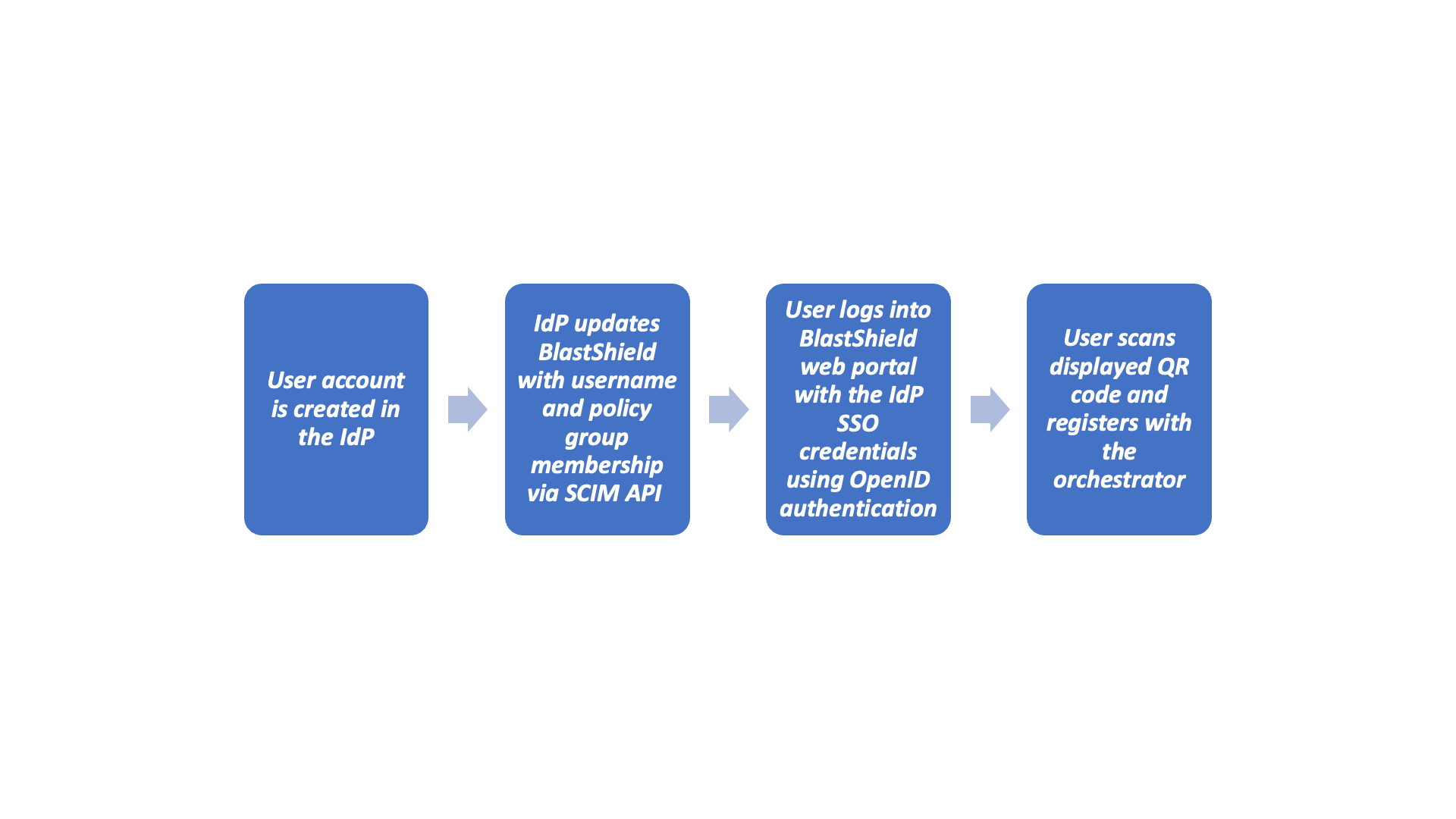
The user will then login to BlastShield using MFA with the Desktop Client and Mobile authenticator. User profile updates made in the IdP are automatically pushed to BlastShield.
The following updates to user information are currently supported:
Username
Policy group membership
When user accounts are deleted in the IdP they are removed from the BlastShield™ orchestrator. Pushing changes from the orchestrator to the IdP is not supported.
Support for external identity providers is in the Professional and Enterprise plans.
Click here to learn how to enable the Azure AD integration.
Support for running gateways in Microsoft Azure
A Gateway may be deployed as an Azure Virtual Machine instance to provide secure, encrypted zero-trust access with micro-segmentation for other VMs running in the Azure Virtual Network.
Support for running the BlastShield™ Gateway in Microsoft Azure is supported in the Enterprise plan.
Upgrade instructions
Upgrade your BlastShield™ desktop client.
See the following page for details. Update the BlastShield™ Desktop Client
Upgrade the firmware of the BlastShield™ orchestrator.
See the following page for details.Upgrade the Orchestrator firmware
Upgrade the firmware of the connected BlastShield™ gateways.
See the following page for details.Upgrade the Gateway
Upgrade your BlastShield™ host agents.
See the following pages for details.Upgrade an Agent from the host or Upgrade the Agent from the Orchestrator